Key Takeaways
- Restaking Mechanism: Allows ETH stakers to reuse their staked assets across multiple protocols, enhancing security and capital efficiency.
- Actively Validated Services (AVS): Developers can build various services, including data availability layers, oracles, and sidechains, secured by restaked ETH.
- Pooled Security Model: Increases network security by leveraging Ethereum’s validator set for external services.
- Free Market Governance: Validators choose which AVS to support, promoting decentralized security.
- Open Innovation: Extends Ethereum’s security to new applications and consensus protocols.
To get an overview about EigenLayer check out our massive blog post: Ultimate Guide to EigenLayer: Revolutionizing Ethereum Staking and Security
Introduction to EigenLayer
EigenLayer is an Ethereum-enabled protocol that introduces restaking, a newly developed primitive in cryptoeconomic security. This model allows for the rehypothecation of ETH to the Ethereum blockchain’s consensus layer.
This is realized when users choose to leverage EigenLayer smart contracts to restake their ETH to provide cryptoeconomic security to additional applications (various middleware module iterations called actively validated services) on the network.
In essence, EigenLayer generates a free market for decentralized trust via Ethereum stakers to AVS modules that make use of validation and staking services provided by operators.
Therefore, much of EigenLayer’s potential lies in its ability to aggregate and extend cryptoeconomic security via is restaking primitive while providing validation services to new applications (AVSs) built atop the Ethereum network.
To help us better understand how EigenLayer works and the points we touched on above, it's necessary to take a closer look at the protocol’s main components in greater detail:
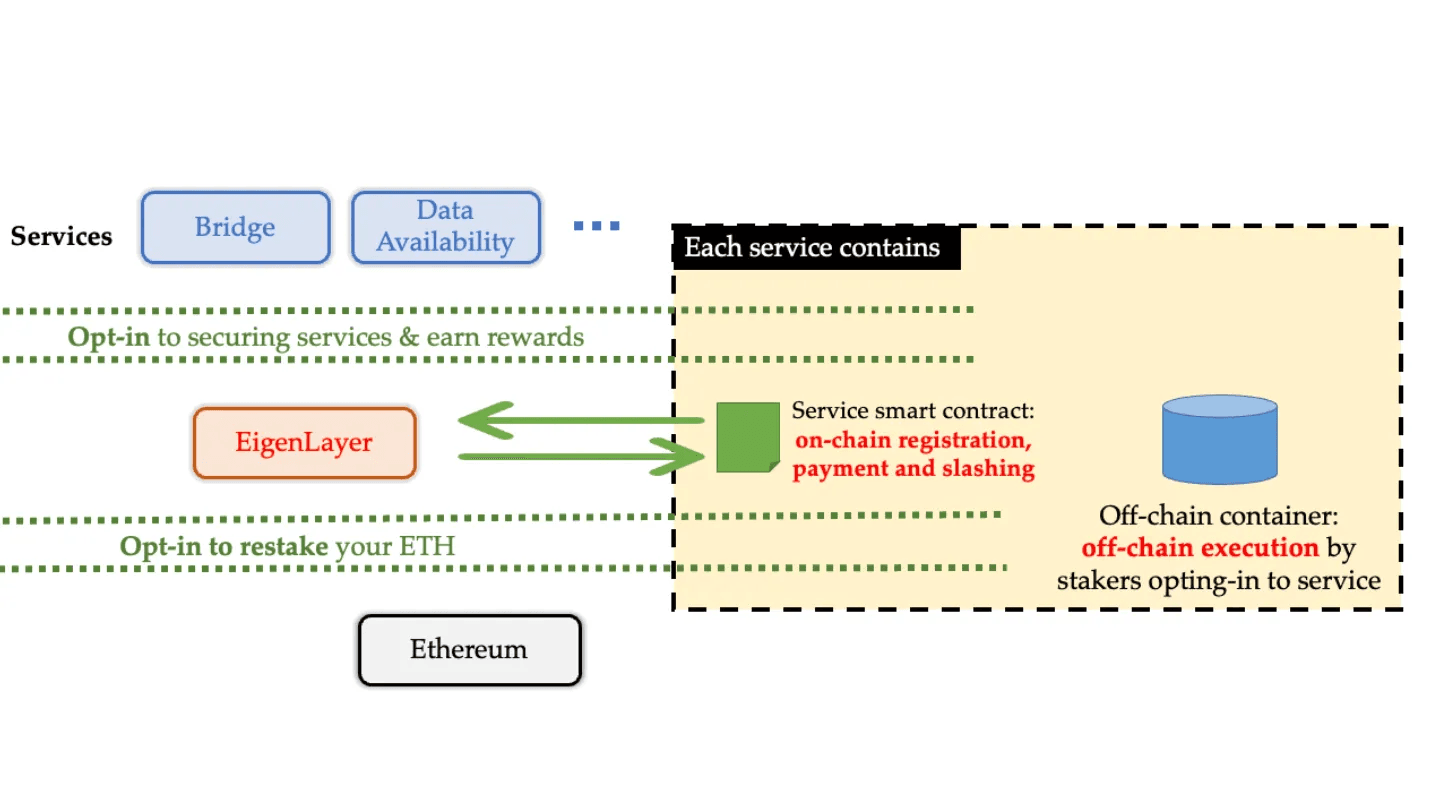
- Operators: Upon registration on EigenLayer, operators enable ETH stakers to delegate their staked assets as either native ETH or liquid staking tokens (LSTs). Operators then opt-in to provide a vast range of services (typically validation services) to AVSs to reinforce the overall functionality and security of their independent networks. Operators are somewhat akin to validators, but instead of validating blocks within an independent blockchain network, they validate and support Actively Validated Services (AVSs) which represent different types of services. Operators are designed to optimize AVSs and increase capital efficiency by reducing their costs.
- Actively Validated Services: Through EigenLayer, developers are able to build (or connect them to EigenLayer) various modules called Actively Validated Services. These can include data availability (DA) layers, bridges, sidechains, oracle networks, trusted execution environments (TEEs), consensus protocols, threshold cryptography schemes, keeper networks, secure multi-party computation (MPC) frameworks, newly developed virtual machines, and more.
- Restakers: The EigenLayer protocol allows users to stake ETH across multiple protocols simultaneously using restaking. This framework allows staked ETH to be utilized as cryptoeconomic security within various protocols outside of Ethereum in exchange for rewards and protocol fees. Restaking can be leveraged by users for both natively staked ETH (by depositing 32 ETH into an EigenPod) or liquid staking tokens such as cbETH, stETH, lsETH, mETH, and others.
- AVS Consumers: On EigenLayer, AVS consumers are essentially users that make use of the various types of AVS modules (i.e., different types of services connected to the network).
- AVS Developers: EigenLayer provides developers with accessibility to Ethereum’s staked capital and decentralized validator set, making previously inconceivable consensus mechanism designs possible though the EigenLayer trust network. Developers play an important role in the long-term value proposition of the network because they are tasked with building different types of AVSs to support the larger EigenLayer protocol.
- Delegation: Like any Proof of Stake (PoS) protocol, EigenLayer leverages delegation whereby stakers delegate their staked ETH or LSTs to operators or run delegation services themselves (as an operator). For this process to work as intended, both parties must mutually agree and opt-in to support one another. In addition, restakers retain control of their stake and select which AVSs they opt-in to validate for.

Fractured Trust Networks and the Evolution of Blockchain
For the first time, Bitcoin pioneered a decentralized peer-to-peer (P2P) blockchain network that introduced unalterable trust to its network participants. However, Bitcoin was application-specific, meaning it was designed only as a store of value (i.e., digital gold) and peer-to-peer payment network. Because Bitcoin lacked programmability, it meant that any decentralized application (dApp) that sought increased utility required a new blockchain that leveraged its own trust network.
Ethereum’s Innovation in Blockchain Systems
In 2015 the Ethereum blockchain launched after 2 years of development, bringing with it the ability for developers to programmatically create their own decentralized applications atop its network via the Ethereum Virtual Machine (EVM). This allowed for fully adaptable modular application development on the Ethereum trust network that extended far-reaching pooled security for all protocols, dApps (think Compound, Aave, and others), and the like built on the network.
The development of Ethereum decoupled innovation and trust and became the impetus underlying the decentralized pseudonymous economy. Essentially, this is because dApps are deployed on the Ethereum network via a trust-fee exchange model whereby the blockchain supplies trust, while dApps are charged a fee to use the network (often through the processing of network transactions and other mechanisms).
Ethereum Layer 2’s as a Paradigm for Scalability and Fee Reduction
The Ethereum Layer 2 era provisioned the usability of rollup-centric scaling architecture by outsourcing execution to a single node (i.e., a centralized sequencer) or a small set of nodes able to absorb Ethereum trust by proving computation through an EVM smart contract utilizing cryptographic guarantees (through validity proofs and zk-rollups) or cryptoeconomic guarantees (through fraud proofs and optimistic collups).
This innovation exponentially increased the number of rollup and proving technologies in the industry and also vastly increased the number of applications that could be built on Ethereum because it dramatically improved scalability and reduced gas fees that the mainchain struggled with.
The Fractured AVS Middleware Service Module Landscape
Outside the confines of Ethereum exists a wide range of service modules known as Actively Validated Services. These services can be thought of as middleware that supports the intersection between blockchains and the dApps operating on their networks.
These can include data availability (DA) layers, oracle networks, consensus protocols, bridges, sidechains, trusted execution environments (TEEs), threshold cryptography schemes, secure multi-party computation (MPC) frameworks, keeper networks, virtual machines, and others.
Because they exist outside of Ethereum, these module components are susceptible to certain limitations, mainly the fact that they cannot make use of the pooled trust network that Ethereum provides (i.e., security).
These modules typically require the processing of inputs derived from outside of the Ethereum network (they must make use of the services that middleware provides (e.g., oracles for asset pricing within a wallet) to connect themselves and the blockchain). Consequently, their processing requirements cannot be validated within the Ethereum mainchain because they don't use Ethereum for security, they just provide a service to users of the network.
Generally, these modules require actively validated services that provision their own in-house validation semantics to complete verification. In addition, these actively validated services are permissioned (confined) in nature or are secured via their own tokens.
In the section below, we’ll explain the differences between the cryptoeconomic pooled security model and the approach taken traditionally when the pooled security framework is not employed.
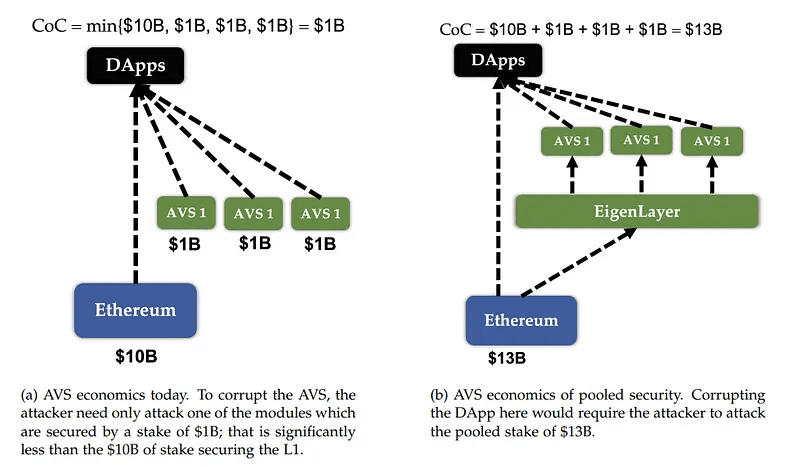
For this to all make sense, it’s important to note that when an attacker attacks an AVS (or dApp) there is a predetermined cost depending on many factors that the attacker must consider. This means in order to corrupt an AVS or application and take control of it (or take control of its assets), the attacker must have a certain amount of capital and fulfill additional requirements in a best case attack scenario. This is called the Cost-of-Corruption (CoC).
Therefore, when the CoC is much higher than the Profit-from-Corruption (PfC), the system is considered to be robustly secure. In essence, this means that if the potential challenges the attacker must undertake are much larger than the potential reward, it is not really worth carrying out the attack in the first place.
Within the present AVS landscape, four main challenges exist that are related to the above idea, including:
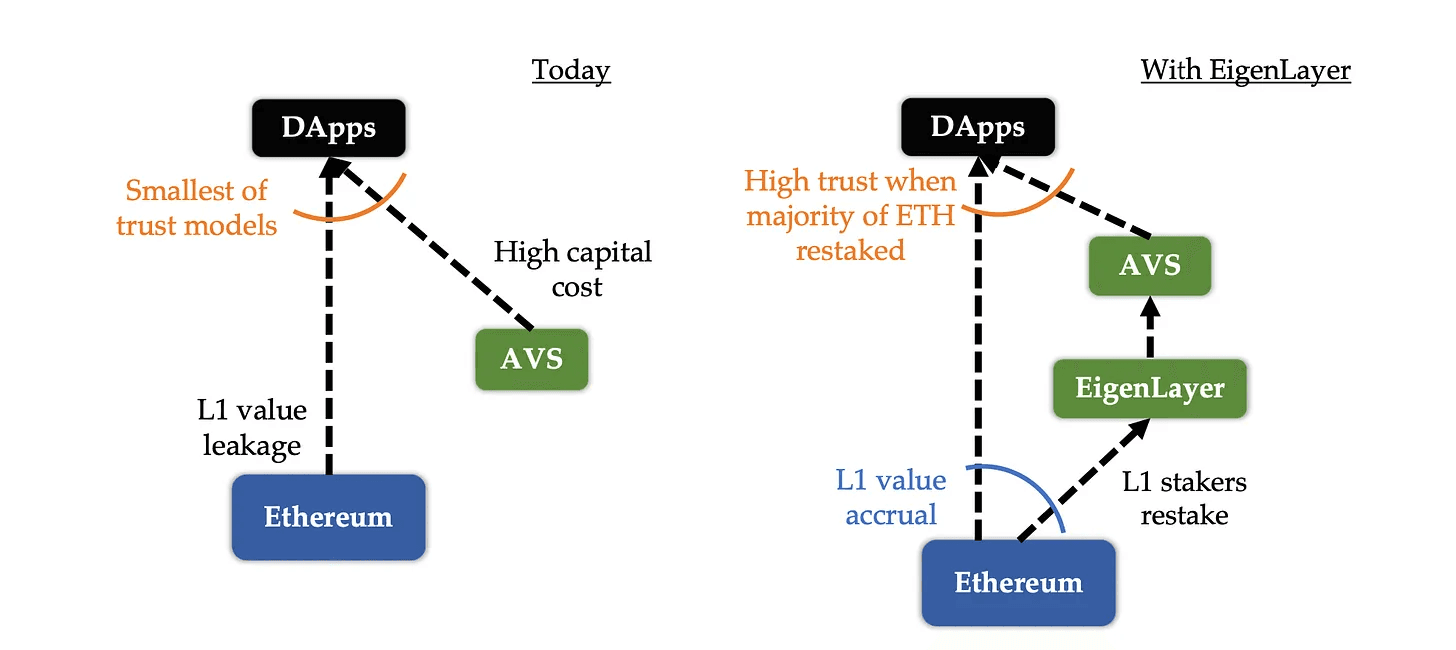
- AVS bootstrapping issues: Developers who choose to develop a new AVS must bootstrap a new trust network to obtain the security guarantees they desire.
- Network value loss: Because each individualized AVS develops its own trust pool, users are required to pay fees to these pools in addition to transaction fees to Ethereum, resulting in value loss from the Ethereum network.
- Dramatically increased capital cost: Validators who stake to secure a newly launched AVS must incur significant capital costs equivalent to the opportunity cost and price risk associated with staking within a new system. This means the AVS must provide a staking return that is more than sufficient to cover this increased cost. Typically, the capital cost for providing staking services is much higher than any operating cost. Case and point, if a data availability layer hosts 5 billion in staked capital to secure its services and the annual percentage return (APR) anticipated by stakers is 10%, the AVS is required to pay at a minimum, 0.5 billion per year to make up for capital cost, a figure significantly higher than its overall operating costs.
-
Reduced trust model for dApps: Unfortunately, the existing AVS landscape exhibits numerous qualities that limit the robustness of dApp security, meaning for example, that any number of dApp dependencies could be susceptible to an attack without the dApp actually taking it head on initially. Therefore, dApp security vulnerability corruption extends largely to the required minimum costs that it would take to overcome one of its dependencies. As an example, this could mean that the costs an attacker must cover could extend simply to the amount staked within an all-important module such as an oracle, instead of having to incur extremely significant costs (the Cost-of-Corruption) to attack Ethereum.
The EigenLayer Solution to Fragmented Trust Networks
As a solution to the four main challenges we touched on above, EigenLayer employs two main frameworks that address these issues head on: pooled security via restaking and free-market governance both of which are designed to augment Ethereum’s security to any system type, while eliminating the efficiencies of existing blockchain governance frameworks.
- Pooled security via restaking: EigenLayer provisions a newly developed mechanism for pooled security by allowing modules to be secured by restaked ETH instead of their own in-house tokens. This means that Ethereum validators are able to set their beacon chain withdrawal credentials to specialized EigenLayer smart contracts called Eigen Pods and also opt into (by choice) new modules (AVSs) built on top of EigenLayer. Validators then download and run any additional node software that is required by these modules. After fulfilling these requirements, the modules are then able to inflict additional slashing conditions on the staked ETH within validators who chose to opt into the module (AVSs). This mechanism is called restaking. In exchange, validators accrue additional revenue for providing security and validation services to their chosen modules. When combined with an on-chain verifiable slashing mechanism, this restaking system enables a much deeper transfer of cryptoeconomic security. As an example, if the module presents as a data availability layer, EigenLayer restakers will be granted a payment when data is stored via the module. In return, restakers are at risk of slashing conditions that are provisioned via proof-of-custody. Restaking therefore markedly expands the space that blockchain applications can share pooled security between one another. Consequently, EigenLayer extends open innovation well beyond smart contract-based dApps enabled via Ethereum to consensus protocols, virtual machines, and various types of middleware. As well, any AVS employing an on-chain slashing contract can benefit from the security guarantees of EigenLayer.
- Open free-market: As a decentralized protocol, EigenLayer provides an open market used to govern how the network’s pooled security is provided by validators and used by AVSs. EigenLayer furnishes an unbounded marketplace whereby validators are able to choose whether to opt in or out of each module built on the platform (i.e., they are able to select which AVSs they want to support). All AVSs must work hard to attract validators to support them by allocating restaked ETH to their specific module. Therefore, validators control which AVSs they decide to support by determining which ones are worthy of additional pooled security given the possibility of additional risk (slashing). More specifically, EigenLayer opt-in dynamics provide two critical benefits: 1.) the constant, conventional governance of the core blockchain is improved via a fast and effective free-market governance framework that allows for the launch of newly developed auxiliary capabilities; and 2.) opt-in validation allows new blockchain modules to manipulate diverse sets of resources between validators, ensuring more advantageous security and performance trade offs. These benefits help EigenLayer become a more efficient and equitable open marketplace where AVSs are able to rent pooled security provided by Ethereum validators.
By interconnecting these two above ideas, EigenLayer positions itself as an open permissionless marketplace where AVSs are able to rent pooled security provided via Ethereum validators.
In addition, EigenLayer solves the four main challenges that traditional AVS systems are susceptible to that we touched on above:
- AVS bootstrapping challenges: With EigenLayer, newly launched AVSs are able to bootstrap security from the larger Ethereum validator set, dramatically improving efficiency compared to traditional AVS systems.
- Network value accrual: EigenLayer provides ETH stakers with various additional revenue streams they can participate in, further consolidating the ecosystem’s network effects as a result of a robustly secure AVS ecosystem.
- More efficient capital cost: Because of the fact ETH stakers reuse their capital across numerous services (AVSs), their capital costs are gradually spread out. Specifically, the marginal cost native ETH stakers incur is barely negligible (hypothetically zero, because there is no risk for an honest node to be slashed)
- Trust aggregation: On EigenLayer, because of the fact that a larger pool of restaked capital exists, the trust model is vastly more robust compared to the non-pooled security model. To illustrate the difference between traditional AVS systems (those that don’t leverage pooled security) and those on EigenLayer, in a theoretical example an attacker would potentially need only 1 billion (a much lower Cost-of-Corruption) worth of staked capital to attack an AVS not employing pooled security. However, to carry out a similar attack against EigenLayer, the attacker would need a 13-fold increase in capital or 13 billion (see the diagram explaining this concept above). The end result is that the EigenLayer AVS pooled security model is significantly more robust compared to the non-pooled security model.
Resources
The information provided by DAIC, including but not limited to research, analysis, data, or other content, is offered solely for informational purposes and does not constitute investment advice, financial advice, trading advice, or any other type of advice. DAIC does not recommend the purchase, sale, or holding of any cryptocurrency or other investment.


