Key Takeaways
- Restaking for Security: Users can restake ETH to secure multiple services and earn rewards.
- Rollup Services: Supports decentralized rollup sequencing and data availability.
- Applied Cryptography: Enables advanced cryptographic solutions, including threshold cryptography and secure computation with Trusted Execution Environments (TEEs).
- MEV Management: Offers validators tools to manage Maximal Extractable Value (MEV) extraction.
- AI Inference: Provides infrastructure for decentralized, private AI inference services.
To get an overview about EigenLayer check out our massive blog post: Ultimate Guide to EigenLayer: Revolutionizing Ethereum Staking and Security
EigenLayer: Your Own Layer Realized
Because of its design and intended utilities, EigenLayer strives to create more decentralized, agile, and permissionless innovation on open public blockchain networks.
In German, the name Eigen means “your own.” Therefore, the name EigenLayer roughly translates to “your own layer.” This name is a reference to EigenLayer’s flexibility as a platform that allows for the creation of a host of utilities and services that complement Ethereum’s restaking narrative.
In recent months, EigenLayer has become arguably the most talked about new protocol in the blockchain industry because of its standing as the pioneer of the restaking DeFi primitive.
Restaking is a mechanism that allows protocol users to stake their assets within a specific protocol to allow the network participant to earn yield. In a synergistic win-win relationship, the staker helps enhance the security of the platform (i.e., the more assets staked within a protocol, ultimately the more secure it becomes) by bonding their tokens within, while the network benefits from the increased security the staker provides.
However, restaking expands on this model, whereby after the deposited assets are locked within a specific protocol by a user (e.g. EigenLayer), they are then given a liquid staking receipt token equivalent to the total value of the initially deposited assets from another protocol operating on top of the larger network.
This collateral is redeemable for the initially deposited tokens which users are then able to use within various DeFi primitives (such as lending, borrowing, yield farming etc.). Should the user wish to withdraw their initially deposited assets, they are then able to exchange them for their restaking tokens without an unbonding period.
Regardless of its focus on restaking, the EigenLayer platform is capable of much more than simply restaking. Case and point, EigenLayer is designed to help allow developers to build a wide range of distributed systems without worrying about the complexities involved in hosting their own underlying trust networks.
On EigenLayer, these distributed systems are known collectively as Actively Validated Services (AVSs). Essentially, as is detailed in our previous deep dives into EigenLayer, AVSs are middleware protocols that are built to offer various services to the larger EigenLayer network.
In essence, AVSs help allow EigenLayer to offer a large number of use cases (as different service types) for a wide range of network participants that make use of the platform.
For the purposes of this explanation, we’ll classify these AVSs into five main categories, including:
- Rollup Services: amplifying the Ethereum rollup ecosystem with various services that leverage various aspects of security from Ethereuem’s trust network
- Applied Cryptography: as a means to develop robust threshold cryptographic systems and TEE committees via a network of decentralized nodes
- General Decentralized Networks: provisioning the bootstrapping of various types of distributed networks including prover markets, relayer markets, and security monitoring counsels
- MEV Management: enabling block proposers to employ their input when it comes to block inclusion and block ordering (i.e., verifying the integrity of validator sets in their respective networks to ensure they act in a non-malicious manner)
- AI Inference: ensuring inference models are cost-effective, private, and equitable
As described in our previous EigenLayer blog post (click the link for an overview), AVSs operating on EigenLayer inherit three layers of programmable trust (or a specific combination of the three), including:
- Economic trust - trust from individuals making a commitment to support the EigenLayer network and support their pledges with financial capital (i.e., the total amount of capital staked on the platform).
- Decentralized trust - trust provisioned via the presence of a decentralized network of node operators in geographically isolated independent locations (i.e., the total number of validators and their distribution).
- Ethereum inclusion trust - trust that Ethereum validators (operators) will create and amend a user’s blocks in the same manner it made promises to the user adjacent to the consensus software they are running (i.e., the percentage of Ethereum validator opt-in).
In this larger analysis, we’ll walk through a high-level explanation of how to understand AVS system design and consider this mental model to better explain the different types of AVSs that can be built by blending and combining various types of programmable trust.
Rollup Services
EigenLayer is designed to enable the development of a wide range of all-important services that scale Ethereum, while simultaneously inheriting security from Etheruem’s decentralized trust network (i.e., the Ethereum blockchain). This modular approach improves security and is collectively referred to as 'Rollup Services.’
More importantly, in the section below we’ll explore seven specific Rollup Services:
- Decentralized sequencing
- Data availability
- Fast finality
- Keeper networks
- Watcher networks
- Reorg-resistance
- Inbound and outbound bridges

Decentralized Sequencing
As it stands currently, sequencers are solely responsible for the order of transaction execution on rollup networks, often leading to short-term censorship and manipulation. This is because larger centralized entities typically solely operate sequencers using a single all-important node, meaning overarching control is often the end result.
In general, long-term censorship is realized in rollups via a mechanism that writes transactions directly to Ethereum, meaning these sequencer-specific challenges can be alleviated by utilizing a decentralized transaction ordering service.
Through the decentralized sequencer service type, users send their transactions to a network of decentralized nodes. Notwithstanding, a wide range of decentralized sequencing services with various transaction ordering policies exist. Some examples of these include:
- Approximate first-in-first-out ordering services (e.g. fair ordering protocols)
- Multifaceted ordering services with enhanced censorship-resistance
- Guaranteed MEV reversion to the rollup
- Individual/shared sequencing amongst rollups
- Threshold encrypted transaction ordering
- Automated event-driven activation
When considering the above decentralized sequencing services, decentralized trust is typically inherited from EigenLayer along with reordering protection via economic trust that is inherent on the network.
On EigenLayer, decentralized sequencers are typically built with a quorum of ETH stakers, meaning a single decentralized sequencer quorum is capable of extending the service for a large number of rollups.
In many instances, decentralized sequencers are not required to perform execution and operate solely as an ordering layer where state growth problems do not exist. This means it is possible to create both lightweight and horizontally scaled sequencers on EigenLayer.
Data Availability (DA)
Data Availability (DA) is a core concept in blockchain systems and has become an increasingly important service that protocols, middleware systems, and other platforms utilize to operate more efficiently.
As it relates to rollups specifically, fundamentally, rollups must have accessibility to the data they need and a way to store it in an external environment to help increase protocol performance and mitigate inefficiency.
More specifically, as a means to ensure the correctness of optimistic rollup state execution and ensure the liveness of zero-knowledge rollups and optimistic rollups, a vital prerequisite is the short term Data Availability of transaction blobs which are processed by the rollup.
Of great significance is the ability for rollups to store these all-important data blobs within a predetermined node set dedicated to storing them and serving them for a stated time frame, during which full blob accessibility is possible for any party.
If we examine situations where data-heavy consumer applications such as gaming and social networks typically possess low value per data bit but require a significant amount of bandwidth for state execution. Consequently, these application types generally demand significant throughput, often tens of megabytes per second at a minimum. In order to meet this demand, high scalability data availability architectures that possess robust security are needed.
To fulfill this demand, the DA layer requires economic trust to address challenges such as the lazy operator problem through Proof of Custody, while also requiring decentralized trust to ensure non stop operation.
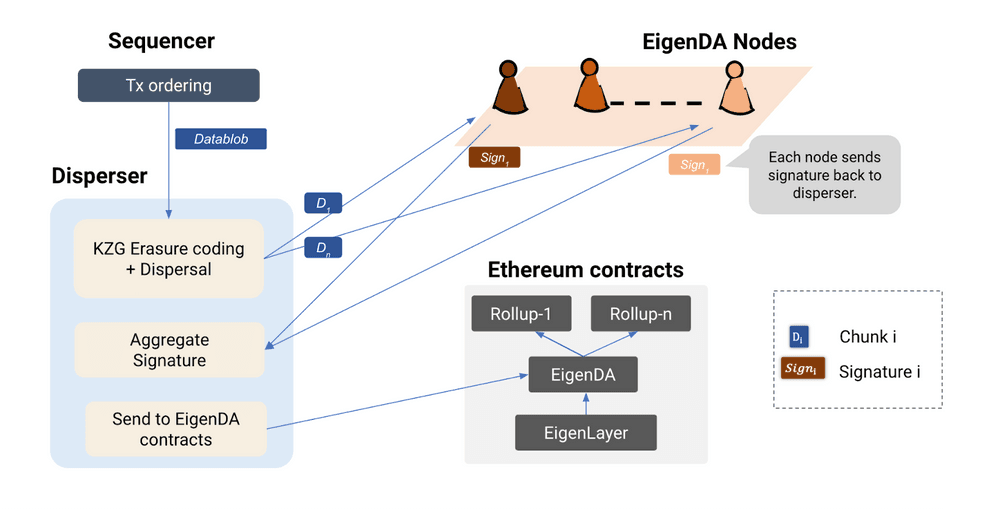
In order to address the continually expanding data availability needs of rollups operating on EigenLayer, the EigenLabs team released the EigenDA data availability framework.
It is possible to develop a hyperscale Data Availability layer that offers a high DA rate combined with a low cost by making use of EigenLayer restaking via a number of leading-edge constructs in DA developed through the Ethereum community (such as Danksharding).
Fast Finality
In recent years, rollups have continued to face a host of immense challenges, including the lack of secure and instant finality, high-priced cross-rollup interactions, liquidity fragmentation across rollup ecosystems, constraints related to ZK verification, and Ethereum finality lag which impacts cross-rollup bridging systems.
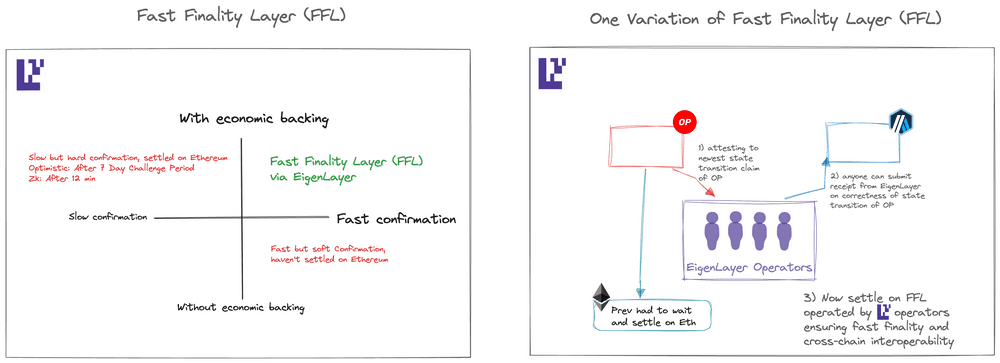
One possible solution to address these problems is through the implementation of a Fast Finality Layer (FFL) atop EigenLayer. With this specific approach, all rollups leveraging the fast finality layer are able to assert a state claim, indicating that a specific block of transactions results in a specific state commitment. When employing ‘fast mode,’ nodes operating within the fast finality layer validate the rollup’s claim, while simultaneously providing attestations to its validity.
In the event a node supermajority attests to its validity, all rollup clients are able to achieve economic finality in a nearly instantaneous manner. Contrastingly, in ‘slow mode,’ attestations originating in the fast finality layer are typically subjected to a challenge period, allowing any party within the network to issue a challenge should they deem malicious behavior could be a possibility.
It is conceivable to visualize single-slot finality, where nodes are required to substantiate the finality of a block through an opt-in mechanism atop EigenLayer. The main premise in this instance would incur that nodes who have restaked are able to then guarantee that they won’t build on a chain that does not include the testified block, therefore creating a prospective finality pathway.
In this design, it is absolutely critical to ensure that the mechanism is 100% opt-in based (meaning the party must choose to participate) and that it does not destroy the underlying legitimacy of the consensus protocol.
It's critical to note that any fast finality layer built on EigenLayer demands high economic trust to ascertain safety.
Keeper Networks
Keeper Networks have continuously demonstrated their significance for those hoping to initiate a set of actions according to specific predetermined conditions. Typically, Keeper Networks deploy nodes in response to 'if-this-then-that' demands.
In general, two types of Keeper Networks exist. With the first type mainly suitable for non-time-sensitive actions, such as initiating challenges towards optimistic rollups via a 7-day window (touched on further in the watcher network section below) or for the management of bridge relays (as touched on in the Relay Network section below). In such instances, the chief requirement is economic trust because of the fact it allows for the penalization of nodes that act maliciously.
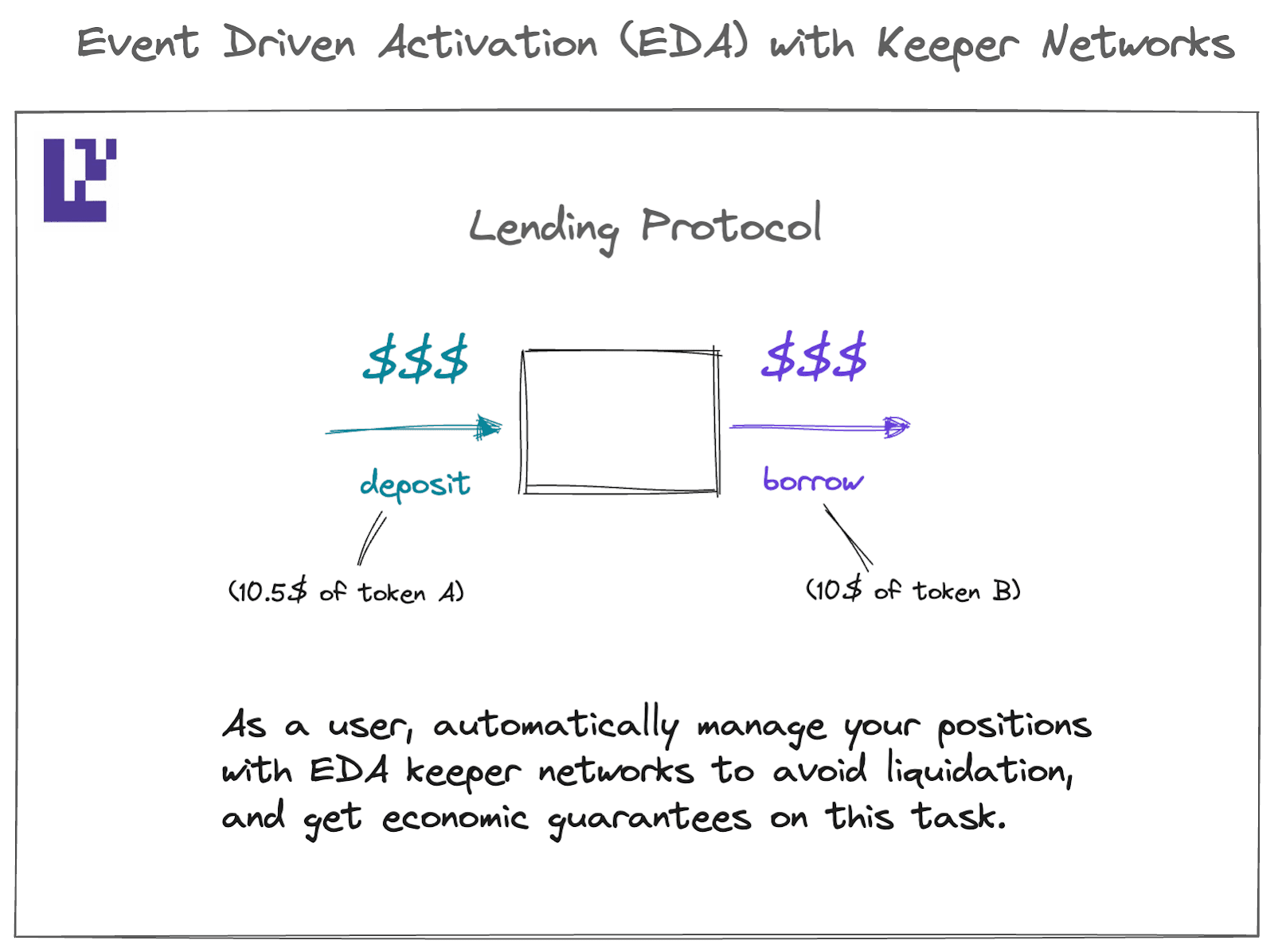
Alternatively, the second type of Keeper Network is built to leverage swift and time-sensitive functionalities (often known as Event Driven Activation or EDA), such as mitigating collateral liquidation, executing token trades, or minting new NFTs in response to certain critically important on-chain behaviors.
Demands of this nature are generally met through Ethereum inclusion trust via EigenLayer, whereby validators are required to fulfill and prioritize such requests. This approach is often used to help reduce the burden of high-cost gas fees that many users are susceptible to.
Watcher Networks
For any optimistic rollup (OR) to be considered secure, a challenge (to potentially dispute the rollups integrity) must be initiated in a pessimistic scenario pertaining to incorrect state execution. This means that all OR clients need assurance that a vigilant group (i.e,. a Watcher Network) is actively monitoring for any possible inaccurate executions and raising challenges if necessary.
This assurance is typically established through economic trust via the appointment of EigenLayer operators as watchers. Nonetheless, to ensure the integrity of the system, operators chosen to act as watchers are susceptible to penalization via slashing if they initiate unwarranted dishonest challenges or fail to raise an appropriate challenge when deemed necessary.
Reorg Resistance
In order to be considered robustly secure, blockchain networks must exhibit chain reorganization (reorgs) resistance. Therefore, when an independent blockchain is able to harness the economic trust provisioned by Ethereum, its security is exponentially increased, dramatically decreasing the chances of a potential chain reorg being successful.
At a high level, it is possible to construct a service (i.e., an AVS) used to ensure nodes possessing a significant stake in Ethereum attest to the block header of the most recently finalized block atop the chain. As a means to realize this, the aforementioned nodes are required to run the chain’s light client to verify that the finalized block has yet to be double-signed and is built atop the most recently finalized block.
Therefore, as a way to confirm the legitimacy of new clients on the chain, block header finalization is necessary to determine if the correct proportion of required EigenLayer stake has attested to the finalized block header.
Consequently, realizing reorg resistance via Ethereum rests on the establishment of economic trust via EigenLayer.
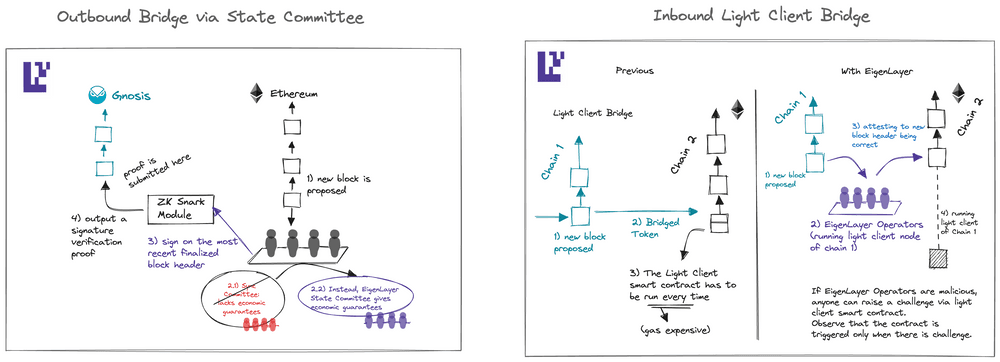
Inbound and Outbound Bridges
Carrying out cross-chain bridging to and from Ethereum implies a delicate balance between security and interoperability. In most instances, centralized bridges extend strong interoperability but suffer from weak security. On the other hand, light client bridges provide robust security but are susceptible to high gas costs required to operate light client smart contracts.
The tradeoff between interoperability and security can be solved by making use of a collection of opt-in nodes, who have provided a large amount of collateralized stake on Ethereum, which are then attested to messages bridging between Ethereum off-chain (in a bi-directional manner, i.e., in and out of the network).
Simultaneously, if they act maliciously and push dishonest attestations they are slashed optimistically on chain, resulting in a process achieved via economic trust. Such instances make use of Ethereum economic trust.
Applied Cryptography
As it relates to applied cryptography, in this section we’ll go over three main tenets of cryptographic primitives built to enhance privacy and safeguard sensitive user data:
- Threshold Cryptography
- Threshold-FHE
- Trusted Execution Environment (TEE) Committees
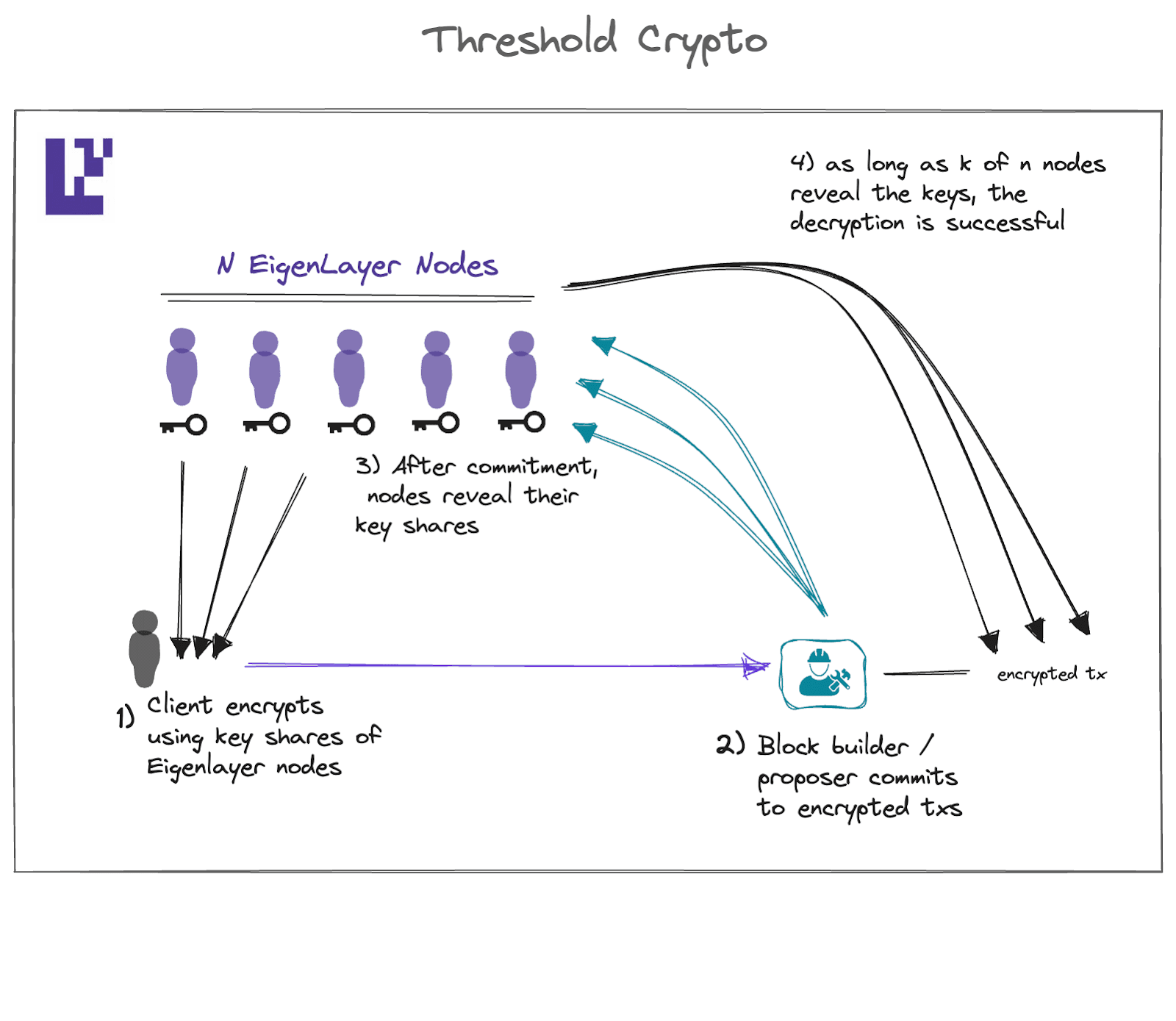
Threshold Cryptography
As many of you know, cryptography is the technology that many computerized systems are based on to ensure their integrity (i.e., by obfuscating the accessibility of sensitive data to malicious actors).
More particularly, threshold cryptography is a type of cryptography that protects information by encrypting and distributing secrets (sensitive data) among a cluster of independent computers or systems to ensure their fault tolerance (i.e., their integrity).
As the name implies, the threshold setting allows individual keyholders to lock a secret in a manner that it's impossible for a single keyholder to open the lock on their own. Rather, it requires a minimum number of keyholders out of the larger keyholder group (i.e., a threshold number) to reconstruct the key and unlock the secret to access the desired data.
Each individual keyholder possesses a key pair made up of a corresponding public and private key where the user’s public keys are required to encrypt the secret, while their private keys are required to decrypt it.
Threshold cryptography has many applications including as a commit-reveal system for protection against targeted frontrunning, privacy issues, and the like.
The core concept analogous to threshold cryptography is that, when considering an encrypted message, at least k (where k = the minimum number of participants required to reform the secret) out of n signers (where n = a fixed number of participants) are able to efficiently decrypt the message. On the other hand, any number of participants less than k are unable to carry out the description process successfully.
Threshold-FHE
More largely, Threshold Fully Homomorphic Encryption (FHE) allows for distributed computation to take place synergistically during data encryption. By combining distributed computation and encryption, robust privacy guarantees are achieved. Because threshold-FHE makes decentralization necessary, EigenLayer provides a reliable and dependable source of decentralized trust.
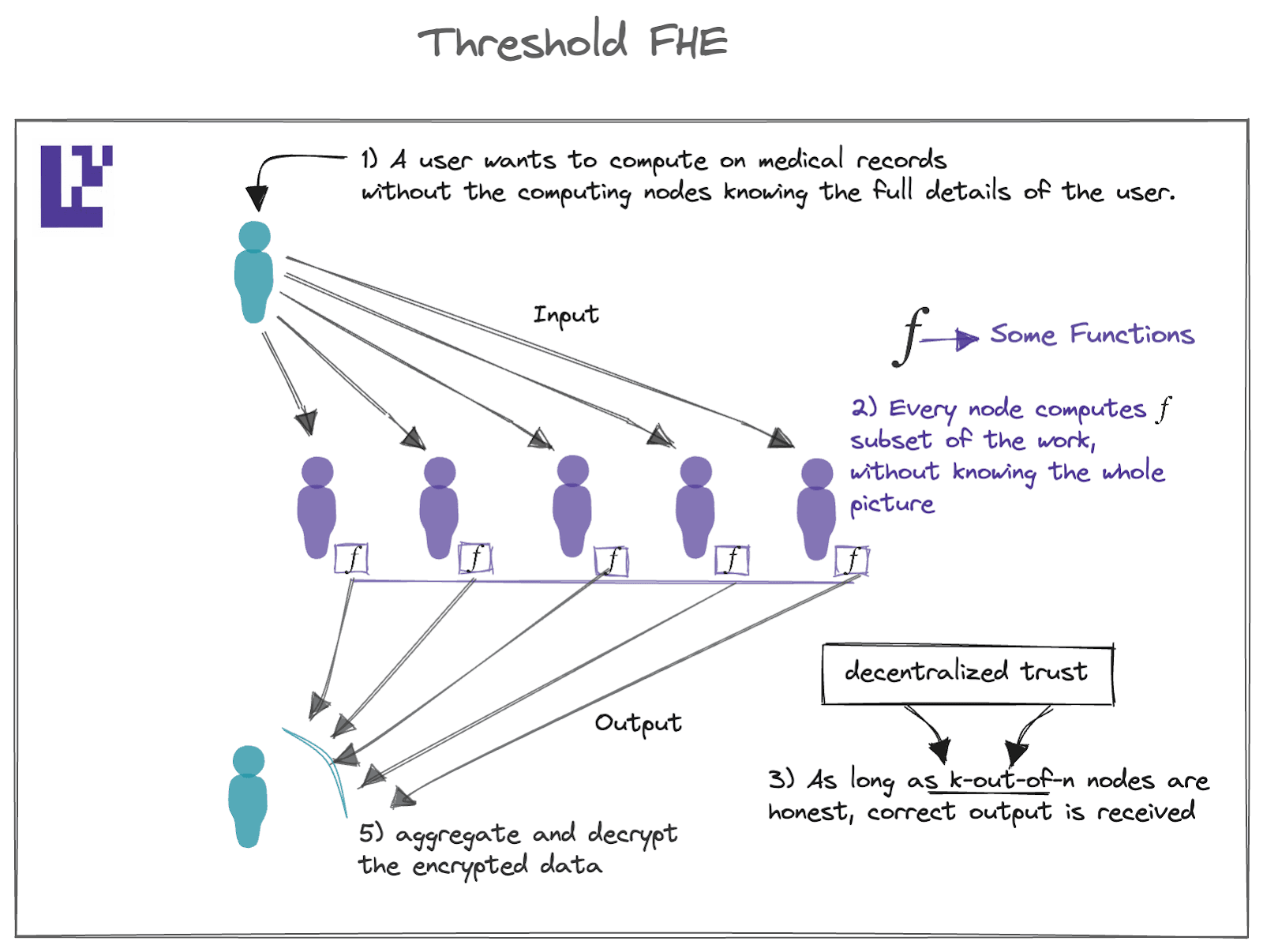
By utilizing the above mechanism, sensitive data is encrypted through the security guarantees of threshold encryption, with the individualized shares of the secret key being distributed between the decentralized network of EigenLayer operators. Afterwards, computations are performed on the encrypted data, ultimately preserving all-important privacy and security.
Trusted Execution Environment (TEE) Committees
Protocols are able to institute robust security guarantees by leveraging Trusted Execution Environments (TEEs), but also through the development of a larger network of TEEs atop EigenLayer (known as TEE Committees).
The synergistic combination of TEEs and distinct TEE committees dramatically enhances the reliability of any committee not harnessing a TEE because a system breach necessitates that both the majority of the committee are colluding, and moreover that the security framework of the TEE has been compromised.
It's important to note that it is possible to require numerous individual TEE models such as Intel SGX, Amazon Nitro, and ARM TrustZone within the TEE Committee and require, at a minimum, one sign-off from each individual model to ensure that compromising the system requires breaking the aforementioned trust models in the presence of majority collusion.
In general, the decentralization of the TEE Committee can be realized via decentralized trust on EigenLayer, while the economic trust can be borrowed from EigenLayer in situations where slashing is deemed a possibility.
In this model, the TEE Committee also provides privacy in the normal mode to ensure the TEE is not attacked. This ensures the TEE represents a robust solution that addresses a variety of issues where both program integrity and privacy are required.
General Decentralized Networks
In this section, we’ll go over some of the network types that EigenLayer and its wide-ranging field of AVSs can enhance. These include:
- Relay Networks
- Prover Networks
- Risk and Transaction Simulation Networks
Relay Networks
Within blockchain systems, bridges often rely on a centralized group of relayers. When an application developer chooses a specific bridge to make use of to compliment their newly designed iterations, their choices are restricted to the options provided by that particular bridge.
This limitation exists partially because establishing a bridge with a specific set of relays is often quite demanding. To improve system reliance, bridges are able to make use of a network of decentralized operators via EigenLayer.
Prover Networks
In the not-too-distant future, it is possible that a host of prover networks will enter the blockchain arena competing with one another to generate zk proofs as quickly and cost-effectively as possible via various parallelization models.
EigenLayer is able to support networks of this type by underpinning their underlying infrastructure through the decentralization of EigenLayer nodes to provide broader access to a host of provers, while simultaneously ensuring network liveness.
Risk and Transaction Simulation Networks
Banks and related institutions typically leverage sophisticated transaction risk analysis systems to help eliminate the possibility of malicious transactions taking place. This is actually a framework that most blockchains simply do not utilize.
Through EigenLayer, a Risk Module AVS could be designed to address this problem through the engagement of a subset of nodes that were able to simulate transactions and carry out comprehensive risk analysis. This would allow the module to detect if a transaction is potentially malicious or not, while simultaneously alerting the network in the event of a potential infraction.
This Risk Module AVS would allow dApps to subscribe to its underlying risk-mitigation services, meaning that any transaction seeking interaction with said dApp would be required to undergo risk analysis prior to the transaction actually being accepted.
More specifically, transactions would only be accepted when the threshold of k (where k = the minimum number of participants required to reform the secret) out of n (where n = a fixed number of participants) nodes signs its correctness.
MEV Management
In blockchain systems, at times, validators implement a strategy called maximal extractable value (MEV) that increases their profitability by deliberately including, omitting, or changing transaction ordering during block creation. This is done to extract additional rewards for themselves on top of the value they would normally obtain via transaction fees.
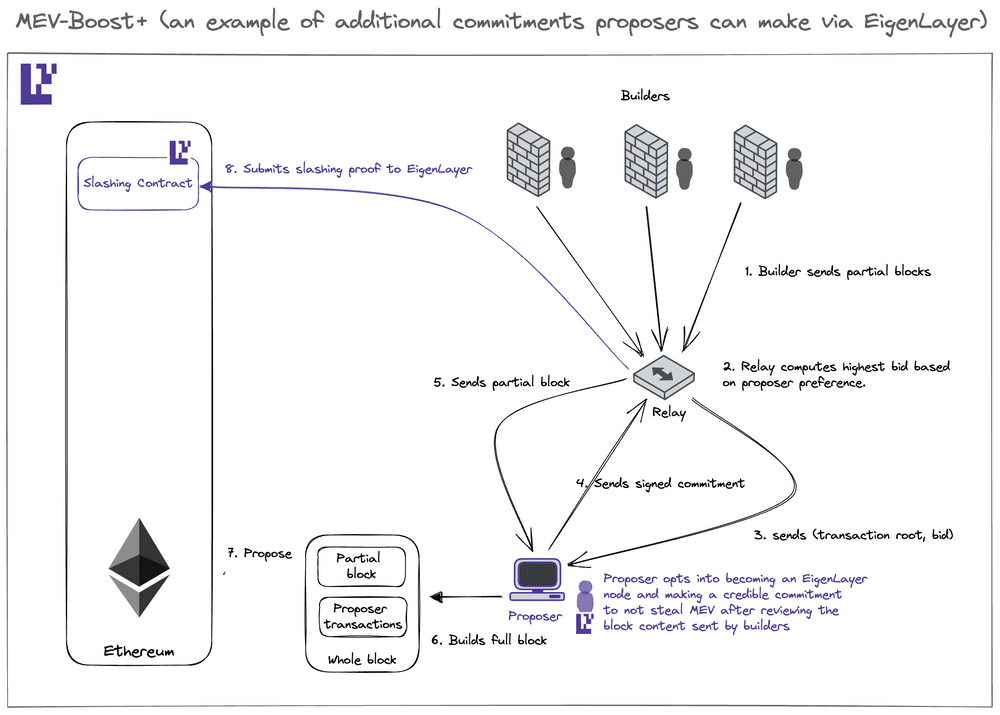
Case and point, within the existing MEV supply chain, validators are only able to extend a limited commitment, meaning they will not take part in double-singing of conflicting block headers (equivocation). Services like MEV-Boost and others are built to rely on this firm commitment.
EigenLayer is designed to expand upon this framework by allowing validators to create a more flexible range of commitments to their counterparts, whether being builders or users specifically.
This expansion of various model types within the MEV supply chain allows for the newfound development of various MEV mechanisms encompassing the “multiple lanes” paradigm, enabling validators to convey their preferences more thoroughly by considering the following:
- Multi-lane block proposal - by leveraging MEV-Boost’s full and partial block auction systems such as MEV Boost +/++, proposers become more incentivized to contribute to block composition, ultimately resulting in stronger censorship resistance
- Event-driven activation - allows Ethereum validators to serve as attributable keepers, ultimately allowing them to activate specific event-driven transactions
- Blockspace futures purchasing - allows for the conversion of statistical arbitrage into atomic arbitrage
- Threshold encryption - enables greater protection against targeted frontrunning in sandwich attacks
Ultimately, the first three MEV mechanisms touched on above rely on Ethereum inclusion trust through EigenLayer, while the fourth relies on decentralized trust.
AI Inference
In recent years especially, artificial intelligence (AI) has become particularly important to the continually evolving technological paradigm the world finds itself in. Highly important to AI in general, is the interconnected relationship between AI training and AI inference.
AI training allows AI models to make factually correct inferences, while AI inferences allow AI models to produce predictions or conclusions based on the data they are given, while algorithmically providing a conclusion to their legitimacy.
Unfortunately, the AI inference landscape consists of a plethora of large-scale mega-conglomerates that operate most of the world’s AI inference engines (think Amazon, Google, and others). The global landscape needs other options to help mitigate this centralized approach.
Therefore, a host of compelling reasons exist that support the operation of AI inferences on-chain. These include:
- Program Integrity: While it is quite common for many services to utilize centralized services like AWS, leveraging zero-knowledge (ZK) Machine Learning (ML) techniques can be cost-prohibitive (expensive). EigenLayer endeavors to augment the market for computational integrity in ML. For those that seek both computation integrity and cost-effectiveness when running AI engines for inference, particularly when relying on
decentralized servers are deemed increasingly risky, EigenLayer offers a viable alternative. By providing a means to inherit economic trust, EigenLayer facilitates these operations.
- Session Privacy: Because of the fact that EigenLayer operators running AI engines are only able to decrypt a full consumer query set if a substantial portion of operators collude, it highlights the importance of decentralization within the system (which EigenLayer inherits via the Ethereum trust network)
- Federated Learning: In any AI engine training model, the presence of multiple actors is critical to ensuring the privacy of data sets. This is because the successful creation of federated training models requires full decentralization of actors within the system. Thankfully, EigenLayer offers this out-of-box.
Closing Thoughts on EigenLayer Uses
The above utilities focused on Rollup Services, Applied Cryptography, General Decentralized Networks, MEV Management, and AI Inference are representative of only a portion of the potential use cases within the continually expanding EigenLayer ecosystem. Unlike any other ecosystem in the blockchain sphere, the limitations of what is possible atop the EigenLayer trust network are only restricted by your imagination.
As a multipurpose toolkit that allows developers the world over to craft their own protocols and services through programmable trust focused on decentralization, economics, and Ethereum inclusion trust, EigenLayer takes what is possible with blockchain to the next level.
Resources
The information provided by DAIC, including but not limited to research, analysis, data, or other content, is offered solely for informational purposes and does not constitute investment advice, financial advice, trading advice, or any other type of advice. DAIC does not recommend the purchase, sale, or holding of any cryptocurrency or other investment.


