Consensus is the foundation of any blockchain, ensuring all participants agree on a single source of truth, even in the presence of faulty or malicious actors. MonadBFT introduces a next-generation Byzantine Fault Tolerant protocol that delivers faster finality, higher throughput, and stronger security than many existing solutions. This article explores its design, innovations, and performance advantages.
Key Takeaways
- Fast and efficient finality – Speculative finality in one round and full finality in just two rounds.
- High throughput with pipelined consensus – Overlapping rounds keep block production continuous.
- Scalable validator participation – Linear communication complexity supports large validator sets.
- Robust safety and liveness – Timeout Certificates and NECs prevent tail-forking and ensure fault recovery.
- MEV-resistant and accountable – Design reduces MEV vulnerabilities and enforces validator accountability.
In the rapidly evolving landscape of distributed systems and blockchain technology, consensus mechanisms serve as the backbone that enables networks of independent nodes to agree on a single, consistent state. Among the most critical challenges in this domain is achieving Byzantine Fault Tolerance (BFT) – the ability to maintain system integrity even when some participants fail or act maliciously.
The importance of BFT cannot be overstated in decentralized networks. A Byzantine fault is any fault presenting different symptoms to different observers, making it particularly challenging to detect and handle. The theoretical foundation for BFT stems from the Byzantine Generals' Problem, where multiple generals must coordinate an attack despite the possibility that some among them might be traitors seeking to sabotage the mission.
Traditional BFT solutions, while mathematically sound, have struggled with practical limitations including scalability, latency, and vulnerability to specific attack vectors. MonadBFT represents a significant advancement in this field, combining theoretical rigor with practical optimizations to deliver a consensus mechanism that supports high throughput, low latency, and enhanced security properties.
Understanding Byzantine Fault Tolerance
Before diving into MonadBFT's innovations, it's essential to understand the fundamental principles of Byzantine Fault Tolerance. Byzantine fault tolerance is the resistance of a fault-tolerant distributed computer system against component failures, where these failures can manifest as arbitrary or malicious behavior rather than simple crash failures.
The core challenge in BFT systems lies in achieving consensus when up to one-third of network participants may act dishonestly. Leslie Lamport proved that if we have 3m+1 correctly working processors, a consensus can be reached if at most m processors are faulty, which means that strictly more than two-thirds of the total number of processors should be honest. This mathematical constraint forms the foundation for all practical BFT implementations.
Traditional BFT consensus mechanisms like Practical Byzantine Fault Tolerance (pBFT) introduced by Castro and Liskov in 1999 established the groundwork for modern blockchain consensus. PBFT operates based on a leader-based voting protocol. In this algorithm, a designated leader node, known as the primary, proposes a block, and other nodes, known as replicas, execute a three-phase voting process consisting of pre-prepare, prepare, and commit phases.
However, classical BFT implementations face several limitations that become pronounced in large-scale, high-performance networks. These include quadratic communication complexity, susceptibility to leader-based attacks, and challenges in maintaining both safety and liveness under network partitions.
MonadBFT: A Revolutionary Approach
MonadBFT emerges as a solution that addresses the fundamental limitations of traditional BFT consensus mechanisms. MonadBFT represents a major leap in Byzantine Fault Tolerant consensus. It is responsible for ensuring that the Monad network aligns on valid proposed blocks efficiently and securely, while supporting 10,000+ tx/s and sub-second time-to-finality, while also supporting a large consensus node set.
Key Innovations and Architecture
MonadBFT introduces several revolutionary concepts that distinguish it from traditional BFT protocols:
Linear Communication Complexity: Unlike classical BFT systems that require all-to-all communication (quadratic complexity), each round follows a fan-out fan-in pattern. The leader sends their proposal to each validator using RaptorCast for efficient broadcast. Validators evaluate the proposal and send a signed vote directly to the next leader. This linear communication mechanism contrasts with other protocols which rely on all-to-all (quadratic) communication; it allows the consensus set to scale.
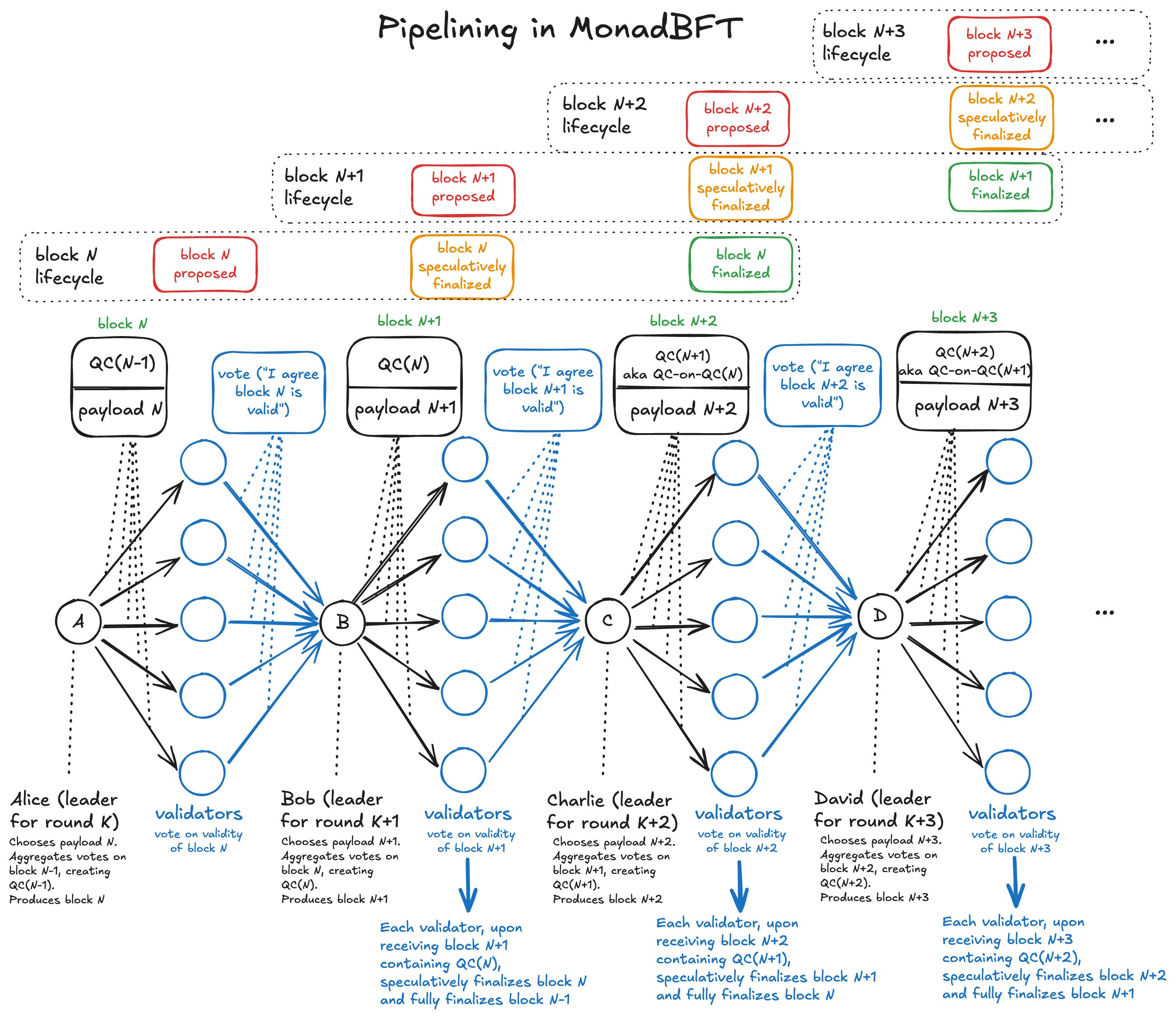
Speculative Finality: One of MonadBFT's most impressive features is its ability to achieve speculative finality in a single round, and full finality in two rounds. This means transactions can be considered final much faster than traditional systems, dramatically improving user experience.
Pipelined Processing: MonadBFT operates as a pipelined protocol where multiple consensus rounds proceed simultaneously. Every round, a new payload and a new QC about the previous proposal gets shared, allowing the parent proposal to be speculatively finalized and the grandparent proposal to be fully finalized.
The Happy Path Protocol
MonadBFT's normal operation follows what's termed the "happy path" - the optimal scenario where all leaders are honest and network conditions are favorable. The protocol operates through a series of rounds, each with a designated leader responsible for proposing blocks.
In a typical three-round sequence, the protocol achieves remarkable efficiency:
- Round K: Alice (the leader) proposes a new block and broadcasts it to all validators
- Round K+1: Bob aggregates votes from the previous round into a Quorum Certificate (QC) and proposes his own block
- Round K+2: Charlie does the same, at which point Alice's block becomes finalized
This pipelined approach ensures that validators can mark blocks as Proposed, Voted, and Finalized in a staggered fashion, achieving continuous throughput.
Fault Tolerance and Recovery
MonadBFT's most significant innovation lies in how it handles the "unhappy path" - scenarios where leaders fail or act maliciously. Traditional pipelined BFT protocols suffer from "tail-forking," where a failed leader can cause the previous leader's block to be discarded, creating opportunities for Maximal Extractable Value (MEV) attacks.
MonadBFT solves this through several mechanisms:
Timeout Certificates (TCs): When a leader fails, validators send timeout messages containing their current view of the network state. The TC includes information on all of the tips from all of the validators contributing timeout messages. The high tip is also computed.
Reproposal Mechanism: When the next leader receives a TC, they are obligated to repropose the highest valid block referenced in the timeout, ensuring that honest proposals cannot be arbitrarily discarded.
No-Endorsement Certificates (NECs): Only when a supermajority of validators attest that they haven't seen a particular block can a leader skip reproposing it, preventing malicious leaders from censoring valid transactions.
Tail-Forking Resistance
MonadBFT combines all of these properties while also being resilient to tail-forking, a critical weakness of pipelined leader-based BFT protocols where a leader can fork away its predecessor's block. This resistance is crucial for maintaining the integrity of transaction ordering and preventing sophisticated MEV attacks.
The protocol achieves this through its sophisticated timeout handling mechanism. The key to MonadBFT's No-Tail-Forking property lies in the handling of the missed slot situation. Intuitively speaking, in MonadBFT, TCs carry enough information to propagate the knowledge of the existence of Alice's block forward even when Bob blackholes all of the votes about it.
CometBFT: The Established Standard
To fully appreciate MonadBFT's innovations, it's essential to understand CometBFT (formerly Tendermint), one of the most widely adopted BFT consensus mechanisms in production blockchain systems. CometBFT is software for securely and consistently replicating an application on many machines. By securely, we mean that CometBFT works as long as less than 1/3 of machines fail in arbitrary ways.
Find out more about CometBFT in our blog post: “CometBFT: The Engine Powering a Multichain World”
CometBFT Architecture
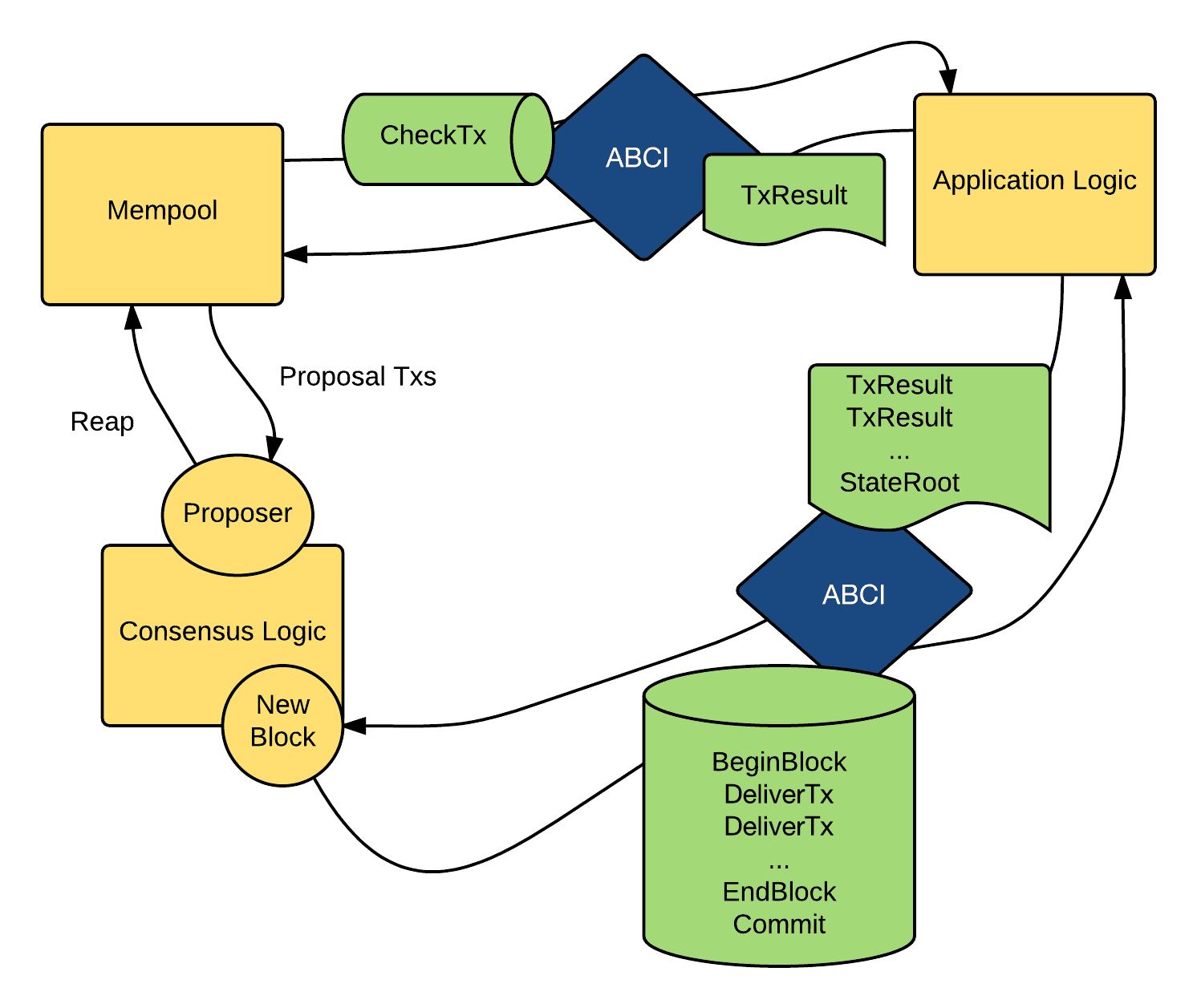
CometBFT follows a more traditional approach to BFT consensus, built upon the Tendermint consensus algorithm. The consensus engine, which is based on Tendermint consensus algorithm, ensures that the same transactions are recorded on every machine in the same order.
The protocol operates through a state machine with the following characteristics:
Two-Phase Voting: Two stages of voting are required to successfully commit a block; we call them pre-vote and pre-commit. There is a picture of a couple doing the polka because validators are doing something like a polka dance. When more than two-thirds of the validators pre-vote for the same block, we call that a polka.
Round-Based Progression: CometBFT advances through rounds where validators take turns proposing blocks. Participants in the algorithm are called validators; they take turns proposing blocks of transactions and voting on them. Blocks are committed in a chain, with one block at each height.
Application Interface: One of CometBFT's key strengths is its modular design. The application interface, called the Application BlockChain Interface (ABCI), delivers the transactions to applications for processing, allowing developers to build custom blockchain applications while leveraging proven consensus.
CometBFT's Limitations
While CometBFT has proven reliable in production, it faces several limitations that become apparent when compared to newer protocols like MonadBFT:
Communication Complexity: Traditional Tendermint-based systems require more communication rounds and messages to achieve finality, limiting throughput and increasing latency.
Block Time Constraints: CometBFT's safety mechanisms often result in longer block times compared to more modern protocols, impacting overall network performance.
Limited Scalability: As the validator set grows, the communication overhead in CometBFT increases significantly, making it less suitable for large-scale networks.
Comparative Analysis: MonadBFT vs CometBFT
The differences between MonadBFT and CometBFT highlight the evolution of BFT consensus mechanisms and the trade-offs involved in their design.
Performance Metrics
Throughput: MonadBFT's configuration demonstrates superior performance with 10,000+ tx/s capability, while traditional CometBFT implementations typically achieve lower throughput due to communication overhead.
Finality Time: MonadBFT achieves finality in 2 slots (800 ms) with speculative finality that can only revert in extraordinary circumstances. This represents a significant improvement over CometBFT's typical finality times.
Block Time: MonadBFT operates with a minimum block time of 400 ms, enabling high-frequency transaction processing that's crucial for modern DeFi applications.
Architectural Differences
Communication Pattern: The most significant architectural difference lies in communication complexity. MonadBFT's linear communication pattern allows for better scalability compared to CometBFT's more traditional approach that can suffer from quadratic communication overhead.
Pipelining: MonadBFT's pipelined architecture allows multiple consensus instances to progress simultaneously, maximizing throughput. CometBFT follows a more sequential approach that, while simpler to understand and implement, sacrifices performance.
Fault Recovery: MonadBFT's sophisticated fault recovery mechanism, including timeout certificates and reproposal obligations, provides stronger guarantees against tail-forking attacks that could affect traditional protocols.
Security Considerations
Both protocols maintain the fundamental BFT security guarantee of tolerating up to one-third Byzantine nodes. However, MonadBFT provides additional security properties:
MEV Resistance: MonadBFT's tail-forking resistance directly addresses MEV attack vectors that could be exploited in traditional pipelined BFT protocols.
Accountability: MonadBFT's design includes mechanisms for detecting and attributing misbehavior, enabling more sophisticated slashing and punishment systems.
Liveness Guarantees: MonadBFT's optimistic responsiveness ensures that the protocol can make progress without waiting for worst-case network delays, providing better liveness properties under varying network conditions.
Conclusion
MonadBFT represents a significant advancement in BFT consensus technology, addressing fundamental limitations that have constrained the performance and scalability of previous generations. Its innovations in linear communication, speculative finality, and tail-forking resistance point toward a future where blockchain networks can achieve both high performance and strong security guarantees.
As the blockchain industry continues to mature and demand for high-performance decentralized applications grows, innovations like MonadBFT become increasingly important. The protocol's ability to achieve no other pipelined leader-based BFT protocol combines all these features – high throughput, low latency, large validator sets, and strong security guarantees – positions it as a significant contribution to the field of distributed consensus.
The information provided by DAIC, including but not limited to research, analysis, data, or other content, is offered solely for informational purposes and does not constitute investment advice, financial advice, trading advice, or any other type of advice. DAIC does not recommend the purchase, sale, or holding of any cryptocurrency or other investment.


