Key Takeaways
- Modular Privacy Framework: Namada offers a customizable privacy layer for blockchains, enabling privacy-focused, cross-chain transactions.
- Zero-Knowledge Proofs: Uses advanced zero-knowledge cryptography for anonymous asset transfers.
- Multi-Asset Shielded Pool (MASP): Supports private transactions for multiple asset types, enhancing interoperability across blockchains.
- Scalability: Utilizes fast proof generation and Byzantine Fault Tolerant (BFT) consensus for rapid transaction finality.
- Interoperability: Includes a two-way Ethereum bridge for secure, private cross-chain asset transfers.
Introduction to Privacy and Interoperability on Namada
One of the main issues that prevents the continued adoption of blockchain systems is their inability to share data between different system types. This problem is solved by building infrastructure that leverages cross-chain and cross-system interoperability. To help address these challenges, Cosmos first began conceptualizing the Inter-Blockchain Communication (IBC) Protocol in 2016.
To expand on the interoperability issues blockchains face, it's important that security, scalability, and privacy are also addressed concurrently. While security and scalability are pivotal considerations when designing state-of-the-art blockchain systems, privacy has become increasingly important in recent years, especially because true privacy is sorely lacking in the majority of production-ready blockchain networks.
Case and point, the inner ethos of the Namada project can be attributed to the availability of privacy as an accessible public good. If it's not clearly apparent, in the data-driven censorship-focused world we live in, the right to equitable online privacy is an underserved human right.
Check out our first blog post Namada (NAM): Privacy-Enabled Interchain Asset Connectivity Unboxed for a deeper introduction.
Namada Privacy and Security Features
As a Layer 1 Proof-of-Stake (PoS) blockchain, Namada approaches the preservation of privacy head on by providing a modular multichain privacy infrastructure set. Ingeniously, Namada is designed to allow builders to seamlessly retrofit privacy into existing digital assets by building a privacy layer across a myriad of decentralized applications (dApps) and blockchains.
Although Namada achieves this goal through several constructs, one of the guiding principles that allows this to come to fruition is the use of zero-knowledge cryptography. Recall that zero knowledge is a specialized way of sending and receiving data (typically for the transfer of digital assets between blockchains) in a manner that conceals the identity of the receiver, sender, and token amount.
In earlier blockchain renditions, zero-knowledge protocols such as Monero, Zcash, and others provided a solid foundation for privacy-preservation. However, as time went on, it became clear that many older blockchain interpretations needed significant improvement.
Relatedly, one of the main constructs of Namada is based on a privacy-preserving technology originally built by Zcash (which pioneered the use of privacy-preserving shielded addresses that meant transactions were undetectable on-chain) which Namada expanded upon via its intent-centric design.
Most blockchains utilize frameworks that allow them to securely and privately share tokenized assets between chains. However, simply because chain-agnostic tokenized asset exchange is possible, it doesn't mean the current model is sustainable for the new-age digital economy. Namada is designed to flip this construct on its head by allowing any asset type to be shared, used, and mutually exchanged between any blockchain without revealing private transaction data.
Primarily, Namada leverages the synergistic relationship between the Multi-Asset Shielded Pool (MASP) circuit and the Convert Circuit (CC) to realize this goal. The MASP and CC utilize multi-party computation (MPC) as a means to run the Namada Trusted Setup (TS), a technology similar to the framework previously used by Zcash.
Namada Network Scalability
Namada makes use of two main elements to realize extremely fast transaction speeds and block finality: fast proof generation and a specialized form of Byzantine Fault Tolerant (BFT) consensus. Together, these features allow the Namada protocol to generate transaction speeds comparable to Visa.
Fast proof generation is a means of generating cryptographic proofs that validate the integrity and correctness of transactions on-chain. By utilizing sophisticated cryptographic techniques, Namada reduces the computational overhead needed to generate these proofs to obtain rapid transaction confirmation and verification.
In addition, Namada makes use of modern BFT consensus algorithms (by combining CometBFT and Cubic Proof of Stake (CPoS)) to ensure the integrity of network transactions. This system allows Namada to reach a consensus on the validity and order of transactions to provide irreversible finality, reducing the possibility of double spending and transaction rollback.
To enable this highly performant design, Namada employs a similar approach to Anoma by employing fractal instances that generate much smaller nested chains within the main blockchain. This design allows for horizontal scaling to distribute the network’s load across multiple instances to dramatically enhance the overall performance and capacity of the network.
Namada Interoperability
Namada achieves cross-chain interoperability within the Cosmos ecosystem through IBC. This allows the protocol to provision the secure and private sharing of assets and various data types with other blockchains on Cosmos. The privacy-focused features of the Namada shielded set will also increase the interoperability and adoption of Namada and the greater Cosmos network over time because it will incentivize external participants to explore the ecosystem further.
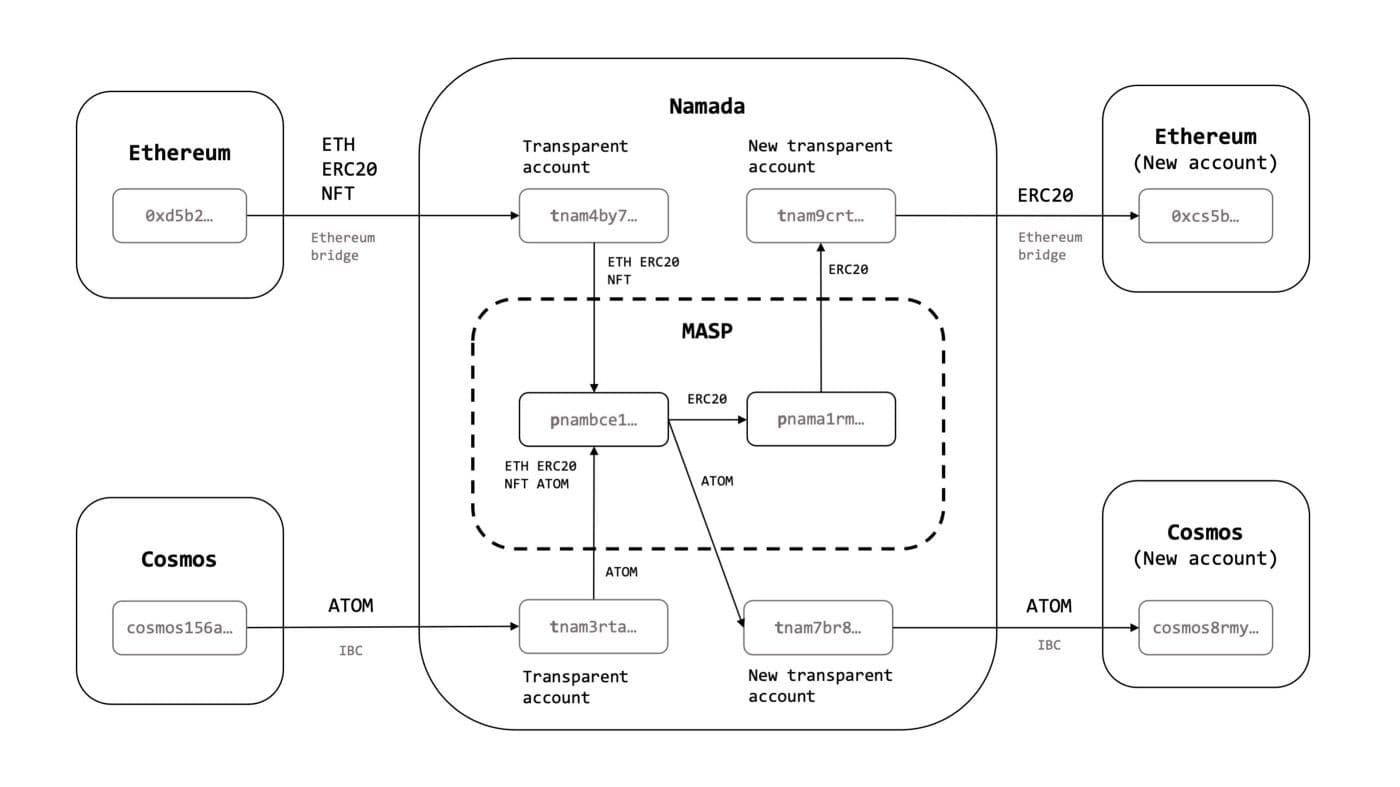
To connect with blockchains outside of Cosmos, Namada is focused on the development of numerous cross-chain bridges over the next several years. To begin this vision, the Namada team recently completed the development of the two-way trust-minimized Namada-Ethereum bridge, allowing users to mint, receive, and shield ERC-20 assets between both networks.
The Ethereum bridge is initially designed to be transparent and open because the platform is in its infancy. As Namada matures, it will become privacy-focused. As has been exemplified on multiple occasions, the development of asset bridges allows for the continued increase in ecosystem-wide liquidity because of increased accessibility from more channels (more blockchains), thus increasing the probability for continued adoption over time.
Anoma’s Technology Examined
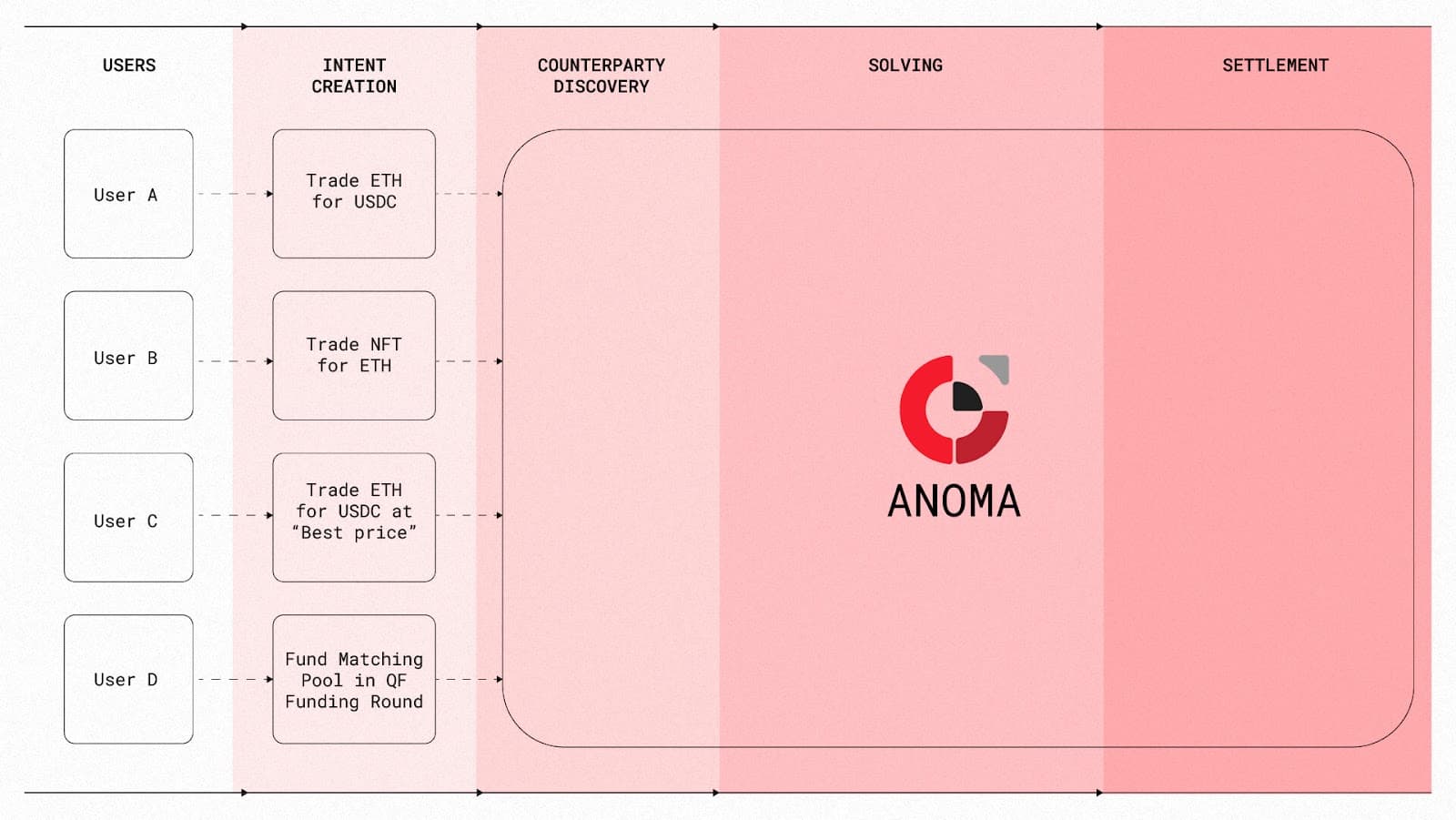
While Namada is a Proof-of-Stake chain-agnostic asset privacy framework, Anoma is built as an intent-centric paradigm for decentralized counterparty discovery (the task of finding another party to trade with), solving, information control, and atomic multi-chain settlement.
In blockchain industry terms, Anoma represents an entirely new paradigm for decentralized computation, flipping the way we interact with decentralized platforms on its head. To accomplish this, Anoma developed an entirely new way of creating programmable infrastructure using intents. This design dramatically expands the capability of privacy-focused blockchains to make them extremely scalable and adaptable.
Instead of focusing solely on the processing of transactions on Anoma — which often employs the execution of specific commands — intents decipher the intention of the command before it is actually initiated on-chain.
This architectural design allows developers to recreate a way of building infrastructure layers by combining privacy-preserving techniques such as zero-knowledge proofs with modularity. This allows for the reorganization of various portions of the stack. Recall that modular blockchains make use of modules to allow for simplified development and customization. The end result on Anoma is a confluence between privacy and modularity, representing a dramatic alteration of how privacy-preserving distributed systems are built.
Understanding the Multi-Asset Shielded Pool (MASP) and Convert Circuit
One of the main concepts behind Namada is as a platform that allows for the private and anonymous exchange of assets on-chain.
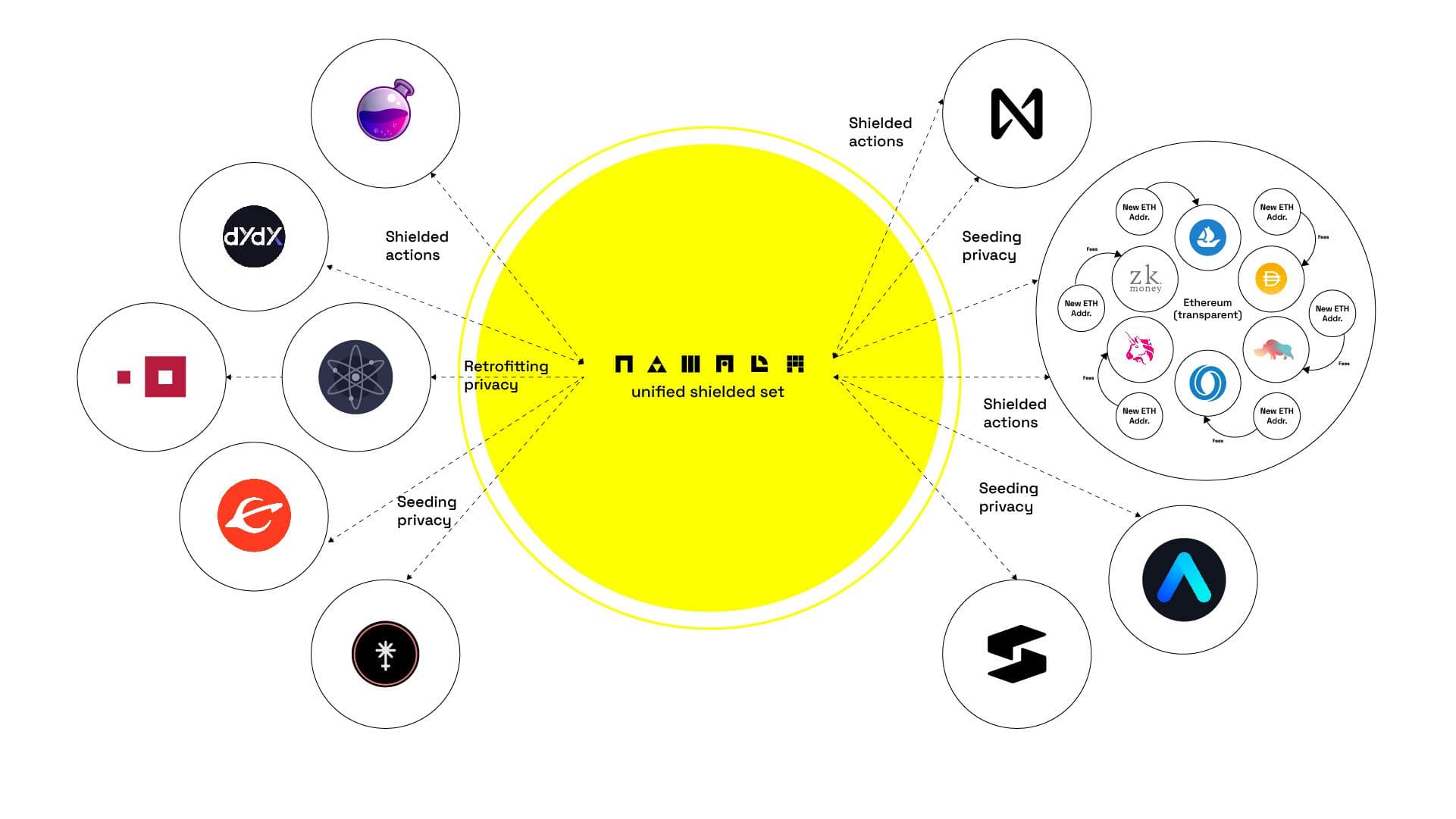
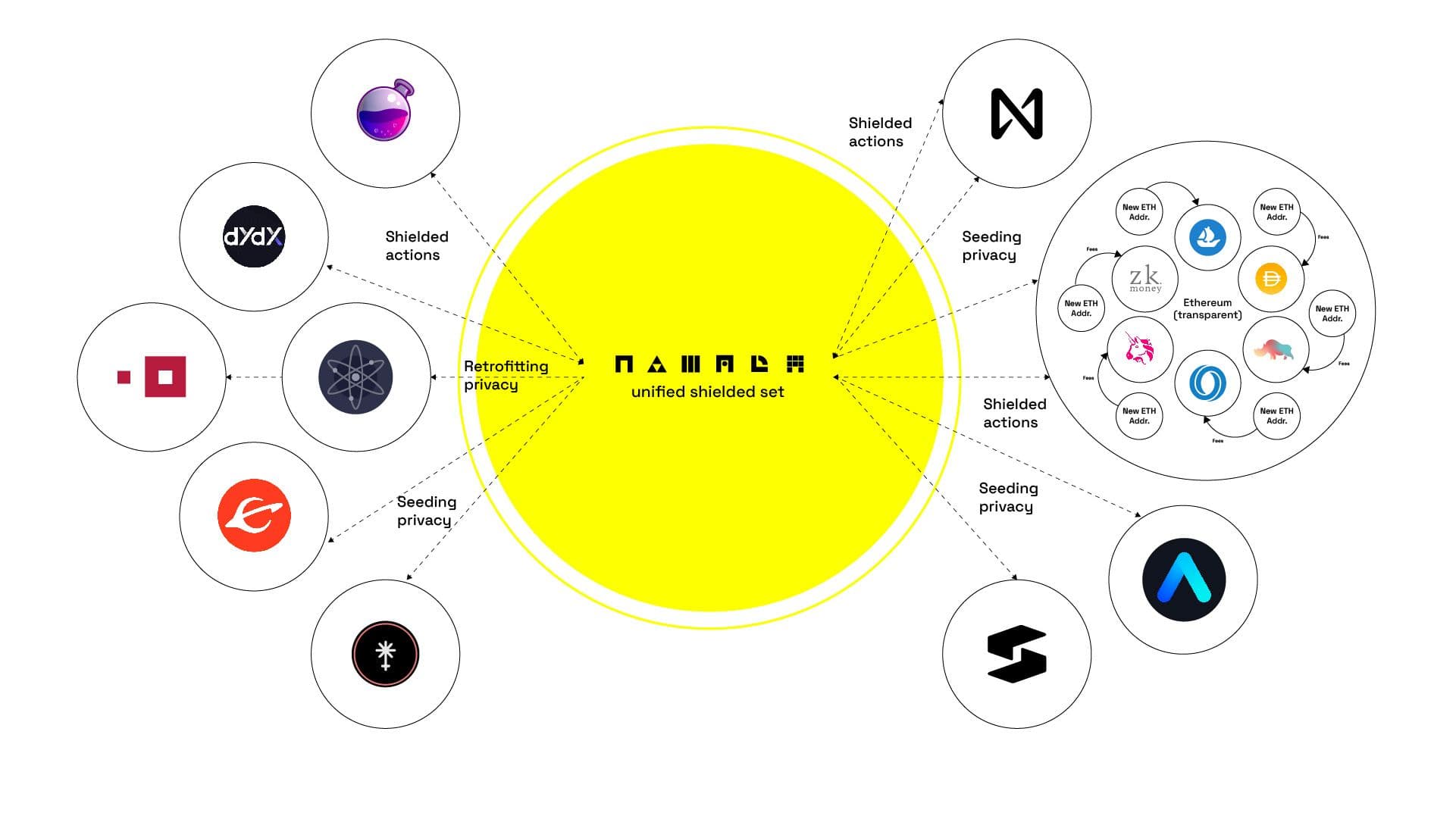
This is realized through a reciprocal relationship between the Multi-Asset Shielded Pool and Convert Circuit. This system is better known as the Unified Shielded Set (USS) and is Namada’s answer to realizing modular privacy in blockchain systems.
Within the shielded set, the MASP and CC circuits work together using specialized zero knowledge proofs to transfer assets without revealing the sender, receiver, or transfer amount. The MASP is modeled after the Zcash Sapling Circuit (Zcash only supported private transfers for the native ZEC token) but expands on the design by enabling multi-assets functionality and programmable asset-conversions.
The MASP circuit is responsible for the minting and burning of shielded assets, while the Convert Circuit is used to facilitate asset conversions in the shielded pool using a predefined conversion table. This model allows transactions in the shielded set to be indistinguishable from one another and eliminates sensitive data leaks.
In simple terms, the MASP allows users to access two main sets (one used to send private transactions and one to send transparent transactions) of assets on-chain:
- The shielded set - allows users to mint assets using a zero knowledge proof that produces a shielded asset called a ”note.” The zero knowledge proof is used to verify the type of asset being sent, the asset amount, and the address that owns the cryptographic proof without revealing sensitive data.
- The transparent set - allows users to mint assets in a transparent manner similarly to a traditional blockchain. This functionality allows users to transfer assets from one address to another, while also allowing for the transfer of assets between bridges deployed on Namada.
This innovative solution eliminates asset fragmentation across different blockchain ecosystems and also creates a privacy layer for DeFi that allows users to interact with a host of transparent chains such as Ethereum, Celestia, Osmosis, and others.
To complement Namada’s Unified Shielded Set, Namada makes use of Shielded Actions (SA). Shielded Actions allow users to execute transactions on-chain to coordinate extremely complex actions between multiple blockchains concurrently. This has many uses, but is especially important for utilities related to decentralized finance.
This system allows blockchains, dApps, and app-chains to maintain a malleable privacy layer throughout the Unified Shielded Set while also enabling a fully adaptable automation layer for user interfaces to greatly expand the overall capabilities of the platform.
Cubic Proof of Stake Consensus
The Namada protocol utilizes a specialized Byzantine Fault Tolerant (BFT) Proof-of-Stake consensus called Cubic Proof-of-Stake (CPoS). CPoS makes use of a customized version of Tendermint called CometBFT that provides peer-to-peer transaction gossip and state machine replication. CometBFT allows the network to exhibit several main improvements at a protocol level. These include:
- Fast finality supports 4-second rapid deterministic finality, ensuring that once a block is committed to the ledger, it is irreversible and cannot be rolled back
- Inter-blockchain communication (IBC) enables full composability with all CometBFT-based blockchains (including all Cosmos-ecosystem chains)
- Battle tested - leverages one of the most reliable, scalable, and secure protocols (Tendermint BFT) in existence used to build Cosmos chains for nearly a decade
- Customizable - ensures high customizability while allowing for the implementation of completely modifiable PoS consensus algorithms which can be tailored to a chain’s specific use
In addition to the above features, CPoS is characterized by several consensus improvements related to epoched staking, cubic slashing, and rewards auto-compounding. Let’s explain:
- Epoched staking - allows state changes to take place only when epochs expire (when a new consensus round begins) to increase light client (less computationally intensive nodes) efficiency. This model also ensures DKG protocols (using Distributed Key Generation) run correctly so transaction mempool encryption and heightened security is established.
- Cubic slashing - is a unique validator slashing mechanism that increases the severity of slashing penalties for correlated dishonest validators (validators working together to manipulate the network) to create a more secure consensus framework.
- Auto-compounding rewards - utilizes a dynamic inflation framework that employs an adaptable inflation system by automatically adjusting the proportion of staked tokens to the total supply via its PD controller mechanism.
The information provided by DAIC, including but not limited to research, analysis, data, or other content, is offered solely for informational purposes and does not constitute investment advice, financial advice, trading advice, or any other type of advice. DAIC does not recommend the purchase, sale, or holding of any cryptocurrency or other investment.