Nillion's technical architecture is built on a dual-layer network, comprising the Coordination Layer and the Orchestration Layer, to facilitate secure and private computations. The Coordination Layer manages network connectivity and governance, while the Orchestration Layer handles data processing using privacy-enhancing technologies. Developers can utilize the Nillion SDK and the Nada Programming Language to create privacy-preserving applications on the network.
Key Takeaways
- Dual-Layer Architecture: Nillion operates with a Coordination Layer for network management and an Orchestration Layer for secure data processing.
- Privacy-Enhancing Technologies: The network incorporates advanced methods like multi-party computation to ensure data confidentiality during processing.
- Developer Tools: The Nillion SDK and Nada Programming Language provide resources for building applications that leverage the network's privacy features.
- Node Diversity: Various node types, including dealer nodes and compute nodes, contribute to the network's functionality and security.
Nillion: An AI-Focused Private Compute Platform
Nillion is a computing network that has been in development since 2021. In this time, the team behind the project pioneered an extremely unique platform that makes use of numerous privacy-focused technologies that work together to achieve a highly advanced framework for computational privacy and its many real-world uses.
Overall, Nillion operates using a dual network architecture design, meaning it harnesses two distinct parallel networks (the Coordination Layer and the Orchestration Layer) responsible for the operational efficiency and foundational architecture of the platform.
To be more specific, Nillion leverages the following foundational components:
-
Nillion Network: The Nillion Network is built on a dual network architecture that utilizes two main layers, including the:
- Nilchain the NilChain Network helps the Nillion Network coordinate the connectivity of the network’s various components. The platform acts as Nillion’s execution environment and is streamlined explicitly to support intra-node use, facilitate payments, network requests, storage operations, protocol governance, blind computation, and network resource coordination.
- Petnet - the Petnet is tasked with orchestration of both internal and external blockchain networks and related environments to expand access to Nillion’s storage and compute. The Petner leverages various privacy-enhancing technologies (PETs) such as multi-party computation (MPC) to allow blind computations to compute sensitive data. Its future vision will take the form as a larger more advanced orchestration layer possessing markedly advanced capabilities.
- Blind apps - the default privacy application structure built to operate on the Nillion Network, blind apps leverage blind computation and numerous types or privacy-preserving technologies.
- Processing Layer - an integral component of the MPC Protocol and the Orchestration Layer, the processing layer allows nodes to be deployed with Nillion’s Node Development Kit (NDK) and connect to a group of clusters (larger node sets) that distribute trust to securely process data throughout the network.
- Nillion MPC Protocol a privacy-focused protocol that utilizes multi-party computation to ensure the cryptographically verifiable integrity of data used on the platform, the Nillion MPC Protocol enhances the capabilities of linear secret-sharing schemes (LSSS) to carry out non-linear operations that evaluate the sum of products of non-zero user inputs to facilitate secure computations for private data in a manner that doesn’t reveal individual inputs (see a more detailed explanation of this concept below).
- The Nillion SDK Nillion’s primary software development kit and tooling system, the Nillion SDK comprises a set of tools (including CLI tools for generating node and user keys, compiling user programs, and other utilities) and libraries that allows developers to build applications via Nillion’s various privacy-enhancing technologies.
- Nilion node types various types of computers (nodes) responsible for upholding the operational integrity of the Nillion network, these include dealer nodes, results nodes, bootnodes, and compute nodes (which can also act as relay servers atop libp2p's Circuit Relay protocol).
- Nada Programming Language an in-house built programming language designed for the development of MPC programs on the Nillion network. The initial implementation of Nada is represented as a Python DSL (Domain Specific Language) but may take another form in its subsequent versions.
- Nada AI and Nada Numpy - a state-of-the-art machine learning paradigm designed to integrate AI model-building via the Nada DSL (Domain Specific Language), Nada AI enables developers to import AI models into the Nillion platform for inference while harnessing the robust utility of Nada Numpy (a Python library designed for algebraic operations that allow developers to perform efficient array manipulation).

To gain a better understanding of Nillion's history and founding and why it's important, consider having a look at our first Nillion article that goes over these topics and much more.
Understanding How Blind Computation Works
To truly understand how Nillion’s technical architecture operates, it's important to be familiar with the concept of blind computation.
More specifically, blind computation allows encrypted computation to be carried out without revealing underlying sensitive data through the use of various privacy-enhancing technologies (PETs) including multi-party computation (MPC), fully homomorphic encryption (FHE), zero-knowledge proofs (ZKPs), and others.
This is the main foundational concept that allows required non-sensitive data to be publicly available while other data is concealed (i.e., typically very sensitive data called high value data) that cannot be shared with any old Sally on the internet.
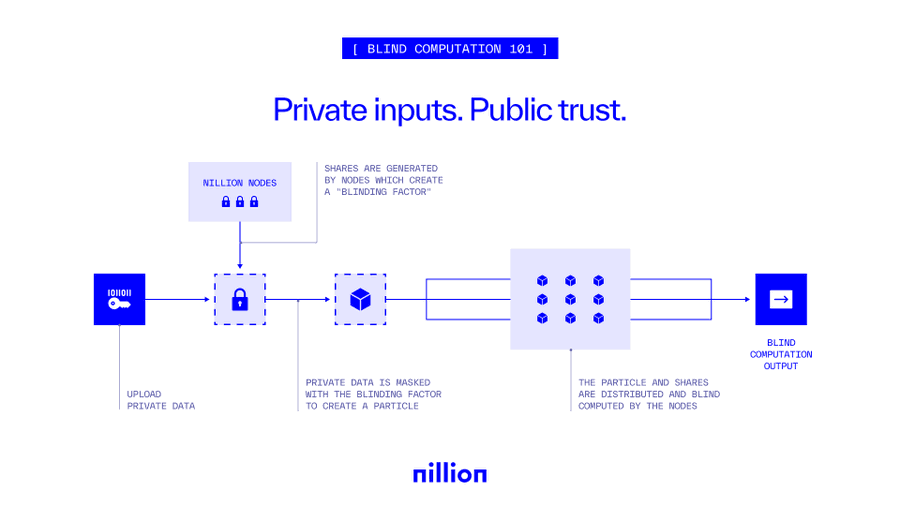
However, for blind computation to work as intended, the Nillion network makes use of an interconnected framework that utilizes several main ingredients responsible for concealing all-important private data. These include:
Masked Factors and One-Time Mask: Both of these elements work together to help secure data during computation on the Nillion network. As it relates to blind computation specifically, data is masked to prevent exposure, allowing computation to be carried out without revealing the actual data being computed. Masked factors are used to apply a one-time multiplicative mask to a factor (a variable that multiplies another variable to change a process's rate or behavior) to maintain computation security to ensure the actual values are not revealed.
Share: In blind computation, shares are responsible for distributing parts of data across a wide range of nodes in the network, with the main purpose being to ensure that no single node is able to access the full dataset, therefore maintaining full information privacy. In particular, these secret shares (separate shares/pieces of data) are facilitated via the linear secret sharing schemes (LSSSs) cryptography method. In general, a share is a result obtained via a node after multiplying the masked factors and adding up the factors of those specific masked factors together.
Sum of Products (SoP): The Sum of Products (SoP) is a mathematical expression harnessed within computations in the blind computation framework where several numbers are multiplied together and then added. Its purpose is to enable complex operations to be expressed simply and securely to guarantee that the underlying data remains protected.
All of the above elements work together by also combining information-theoretic security (ITS) paradigm, and linear secret sharing schemes (LSSSs) via the pre-processing phase and the non-interactive computation phase to help achieve blind computation on the larger Nillion network.
Specifically, as it relates to LSSSs, shares are distributed across numerous participants in a manner where only certain groups of shares are able to reconstruct the secret. The key characteristic of LSSS is linearity, meaning that any linear combination of valid shares results in the formation of another valid share.
Blind Apps
Because Nillion is focused specifically on privacy and fulfilling a wide range of privacy-specific utilities, it developed its own application-focused framework called blind apps.
Essentially, blind apps represent the default privacy-enabled application structure built on the Nillion network. In particular, blind apps run blind computation via one or more privacy-preserving Nada programs (Nada is Nillion’s privacy-focused language). This is realized by allowing Nada programs to compute secret integers without being aware of the underlying input values, creating an ideal environment for the processing of data sensitive operations on the network.
Overall, for a developer to create a blind app on the Nillion protocol, they must carry out the following steps in chronological order: 1.) install the Nillion SDK 2.) initiate the commencement of a Nada project, 3.) build a blind app, and 4.) deploy their newly-created application to the Nillion testnet (and after mainnet launch, deploy on mainnet).
The Nada Programming Language
During development, Nillion created its own proprietary programming language called Nada. In general, Nada is built specifically for the development of blind apps on the Nillion network and is designed to complement the privacy-specific features of the Nillion platform.
Nonetheless, the Nada language is designed to write programs that make use of secret inputs from multiple parties. The term blind computation comes from the fact that these programs compute in a manner that is “blind” (concealed) to the underlying data, signifying they are unable to access or view secret inputs.
While being tailored for AI and other uses, Nada is built to be a MPC-specific language and the initial implementation of the language is built to be a Python DSL (Domain Specific Language). Generally, Nada is characterized by a number of critically important features, including:
- Strongly typed each expression and variable makes use of a special type that is verified at compile time as a mechanism to prevent common errors and type mismatches
- Correctness-oriented built to be focused on correctness and exhibits features such as type-checking and static analysis via the compiler
- Compiled represents a compiled language that makes use of different stages
Nillion’s Dual Layered Architecture
To help the network achieve its vast range of privacy-focused utilities in the real world, Nillion encompasses two parallel interconnected networks. These include:
- Coordination Layer also known as the NilChain Network, the Coordination Layer helps the Nillion Network coordinate the connectivity of the network’s various components. The Coordination Layer acts as Nillion’s execution environment and is streamlined explicitly to support intra-node use, facilitate payments, requests, storage operations, network governance, blind computation, and network resource coordination.
- Orchestration Layer - often called the Petnet, the Orchestration Layer is tasked with the orchestration of the platforms for both internal and external blockchain networks and related environments to expand access to Nillion’s storage and compute. The Orchestration Layer harnesses various privacy-enhancing technologies (PETs) such as multi-party computation (MPC) to allow blind computations to compute sensitive data.
The Nillion MPC Protocol and the Nillion Processing Layer
The Processing Layer allows nodes deployed via Nillion’s Node Development Kit (NDK) to be connected to a group of clusters that distribute the trust needed to securely process data.
Specifically, the Processing Layer is part of Nillion’s Multi-Party Computation (MPC) protocol. It involves two main phases: pre-processing and non-interactive computation. Pre-processing helps the network to prepare to utilize high-value data, while non-interactive computation is a
model of computation where parties perform calculations without directly communicating with one another (see below).
The Nillion MPC Protocol is a privacy-powered platform that harnesses multi-party computation technology to cryptographically guarantee verifiable data integrity on the platform. One of the protocol’s main purposes is to improve the capacity of linear secret-sharing schemes (LSSSs) to help the platform achieve private computation without revealing sensitive information.
During operation, the MPC Protocol makes use of two distinct phases in chronological order:
- Pre-processing phase: This phase involves the generation and distribution of shares (masks) related to each individualized factor and term via the Sum of Products (SoP) expression using standardized MPC capabilities. The pre-processing phase is carried out without input values and depends solely on the number of inputs.
- Non-interactive computation phase: The non-interactive computation phase allows the MPC Protocol to perform calculations based on private inputs. Although the computation is non-interactive where parties don't directly communicate, it does not require message exchanges amongst parties and is designed to align with asynchronous workflows.
Moreover, the Nillion MPC Protocol possesses the following critically important features:
- Non-linear arithmetic functionalities - allows the protocol to assess a sum of hidden inputs without leaking input data to a prospective party
- Efficient preprocessing - allows for the creation of shares to be completely external to input values, while depending separately on the number of inputs (factors and terms) within each term
- Asynchronous computation helps allow the non-interactive computation phase to connect with asynchronous workflows and improve these related processes without requiring message exchange between participants.
- ITS security - helps ensure the protocol supports information-theoretic security (ITS) that is innate in linear secret-sharing schemes (LSSSs) to create a system that is unable to be exploited by adversarial attacks that possess unlimited computing resources

Nilion Node Types
The Nillion network incorporates several distinct node types to support the architecture of the platform. These include:
- Dealer Nodes SDK-enabled nodes responsible for sending tasks to the Nillion network
- Result nodes - SDK-powered nodes reconstruct computation results taking place on the Nillion network
- Bootnodes - nodes designated as entry points to the Nillion network, a list of bootnodes is required by each node that wishes to join the network. Once a node wanting to join the network dials a set of configured bootnodes and connects, that node is introduced to the rest of the network and the inter-node peer to peer discovery process commences.
- Compute nodes - nodes operating on Nillion designed to perform the network’s main functions such as computation and storage and others
- Relay servers (made up of specially configured compute nodes) because dealer and result nodes are able to run in any environment (e.g., web browsers or other platforms), compute nodes can be configured as relay servers via libp2p's Circuit Relay protocol. Dealers and result nodes are therefore able to establish relay circuits with relay servers as a means to operate within the network similarly to other nodes in the system.
All nodes operating within the Nillion network leverage private (node key keeps the private key secret) and public key pairs so they are easily identifiable and cryptographically secure.
The Nillion Software Development Kit (SDK)
To help ensure the proper deployment and development of decentralized applications (dApps) and node systems on the Nillion network, the platform makes use of the Nillion SDK. Namely, the SDK harness the following interconnected elements:
- Nillion CLI tool - a CLI tool that facilitates interaction between the Nillion network and the command line enabling the facilitation of various processes such as network status verification, program upload, and the storage of computational secrets
- Local network allows developers to create a local Nillion Multi-Party Computation (MPC) cluster network
- User and node key generation - various tooling systems used for the creation of node and user keys focused on secret network usability
- Program-simulator - a framework used to locally simulate the execution of Nada programs during development
- Nada compiler - used to compile PyNada (Python/Nada) programs run in confluence with the program-simulator or for those stored on the larger Nillion network
- Python and JavaScript clients - enables the connectivity between node clients and decentralized applications within the network
In addition to the Nillion SDK, Nillion also leverages the Nillion Node Deployment Kit (NDK) as a network node deployment framework.
Resources
The information provided by DAIC, including but not limited to research, analysis, data, or other content, is offered solely for informational purposes and does not constitute investment advice, financial advice, trading advice, or any other type of advice. DAIC does not recommend the purchase, sale, or holding of any cryptocurrency or other investment.


