As our lives in the digital age are so interwoven with everything online, protection of sensitive information has never been more paramount. Every click, every message, and every transaction writes a digital trace that needs protection against prying eyes. This is where private-public key cryptography steps in with all its magic - an invisible shield to the human eye, yet very real, safely protecting our privacy and security.We will be considering how the technology protects our online activities, ranging from transacting with cryptocurrencies to sending confidential emails, making online purchases, and accessing secure websites to protecting our financial transactions.
Key Takeaways
- Public-private key cryptography is one of the few underlying technologies that make digital interactions secure.
- The security of this system is based on complex mathematical concepts and algorithms.
- The system ensure that even if the message is intercepted during transmission, it would only be decrypted and read by the intended recipient.
- Digital signatures use private-public key cryptography that authenticates messages and documents in terms of origin and validity.
- Seed phrases, generated through cryptographic methods, giving rise to multi-currency wallets that safeguard your digital assets.
Cryptography Protecting Your Privacy
The very concept of cryptography implies the implementation of security to information by means of encryption and decryption techniques. Its history spans millennia, with milestones like the Caesar cipher, employed by Julius Caesar, and the Enigma machine during World War II.
The Achilles' heel of traditional cryptography was that, while effective for its own time, there was the major issue of the secure exchange of the keys between the parties communicating. It was this limitation that was overcome with the advent of modern Asymmetric Key Cryptography.
The novel approach uses a pair of mathematically linked keys, eliminating the need for sharing the same key, thus enhancing security. This really provided the paradigm shift that was needed in secure communication. The security of such systems depends on the computational infeasibility of determining the private key from its public counterpart. In such a way, even if an encrypted message was intercepted, it could only be read by the one possessing the corresponding private key.
Today, cryptography is used everywhere, from online banking and e-commerce to secure messaging and cryptocurrencies. But cryptography encompasses much more than just encryption: there is digital signature, a form of digital fingerprint that verifies authenticity and origin of information. It forms the basis for ensuring integrity in data, secure software distribution, and trusted identity verification.
The Dance of Two Keys: A Tale of Encryption and Decryption

Behind the elegance of private-public key cryptography, known as asymmetric cryptography, exists a very interesting world of mathematics. Security depends on complex properties of prime numbers and difficult algorithms.
One of the most widely used algorithms is RSA (Rivest-Shamir-Adleman), depending on the difficulty of factoring large prime numbers. Another one called Elliptic Curve Cryptography, or ECC, which uses shorter key lengths to achieve similar security with better efficiency for resource-constrained devices.
Private-public key cryptography relies on a pair of keys that are associated with each other.
- Public Key is basically the open lock which is shared freely with the world. It's the key utilized when data needs to be encrypted, hence, data would be jumbled into unreadable format. Consider this like a mailbox in which everyone can drop a letter, but only the owner of the private key can retrieve this email.
- Private Key is a one of a kind key, which the owner keeps private and safe. Being the only tool able to decrypt scrambled data back to the precise original readable text.
Such ingenuity of pairs of keys allows for secure communication over open channels in the presence of any malicious and passive interceptor. Only the intended recipient, with access to a unique private key, can decipher the encrypted message and maintain confidentiality.
In fact, cryptography is all around us, hiding under the hood of innovative solutions. And only those who interact with blockchain and cryptocurrencies have a chance to touch it directly in the form of well-known complex keys, where the public key serves as a wallet address and the private key allows access to a balance. Some wallets might use different terms, like secret keys or recovery keys, but they all serve the same purpose.
Private and public keys have different lengths depending on what they are used for. For instance, a Bitcoin private key is 256 bits in length and is usually made of 64 characters in the range 0-9 or A-F, similar to the private keys for Ethereum.
For example, a private key would look something like:
A9F83B46C4D56E7BA1F34C7297A8D32E1B5F2C4578EC9A3B47D1E6C23F8B1A7D
Some wallets give the ability to import or export private keys. They are handy when a user wants to switch to another wallet or restore a lost account.
Worth remembering: private keys should stay away from hands and eyes of others.
How Private-Public Key Cryptography Works
Suppose you want to send a confidential e-mail to a friend. Here's how private-public key cryptography would make it secure:
- You take your friend's public key, which they shared with you, and encrypt the email with it. It scrambles your message into some form of unreadable code, unreadable by anyone except your friend, who has the corresponding private key.
- You send this encrypted email across the internet. Anybody who intercepts it during the transmission will not make out what is inside without having the private key.
- The friend who received the encrypted email decrypts it using his private key. As that is his private key, nobody else could revert the scrambled code into the real message.
This ensures that the encryption is end-to-end, and that the message is protected from all prying eyes on the journey.
Seed Phrases: The Guardian of Your Keys

You may not remember the days when it was necessary to create a pair of keys for each wallet of a chosen cryptocurrency, as in the example above. Thus, there were many wallets with their private and public keys that had to be stored. Seed phrase appeared along with multi-currency wallets and allowed you to access all your wallets. If for some reason it was not possible to restore the wallet, the seed phrase could be decrypted and get public and private keys from all cryptocurrencies of its owner.
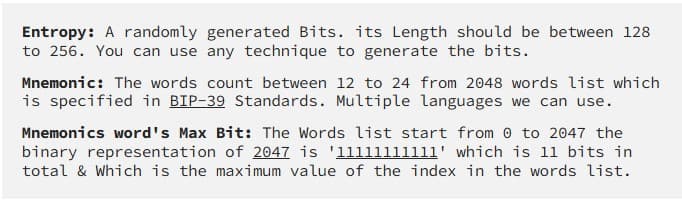
The Genesis of a Seed Phrase: From Entropy to BIP39
A seed phrase doesn't magically appear as a set of words. It begins as a complex, randomly generated number known as entropy. This entropy is then transformed into a human-readable format using the Bitcoin Improvement Proposal 0039 (BIP39) standard. This ingenious process converts the lengthy and complex entropy into a user-friendly list of words, typically 12 or 24, making it easier for users to manage and store their private keys. BIP39 is a widely adopted standard that defines the mnemonic seed phrase format used for generating deterministic wallets.
A deterministic wallet is built on a specific algorithm and seed. All of the keys and addresses created by a deterministic wallet are made from that seed. The practical result of this is that, as long as the user still has access to the seed, a new wallet can be created and all the addresses and keys recovered — even in the event that the original wallet becomes corrupted or lost.
At this point, you might be wondering: if it’s just a literal translation of a long number, what makes a secret recovery secure? Well, actually, that is more to do with how the entropy was generated. To explain, the entropy must be very long and random, otherwise someone might be able to guess it. As long as the entropy is chosen at random and made up of more than 128 bits, it’s sufficiently secure that no person or computer will be able to crack it.
To summarize, private-public key cryptography is the silent guardian of our digital lives, quietly working behind the scenes to protect our information and enable secure communication. As our reliance on technology continues to grow, understanding this essential technology empowers us to make informed decisions about our online security and privacy.
Perusing the intricate workings of private-public key cryptography, we gain a deeper understanding of the invisible forces that safeguard our digital world, allowing us to navigate the vast expanse of the internet with confidence and peace of mind.
The information provided by DAIC, including but not limited to research, analysis, data, or other content, is offered solely for informational purposes and does not constitute investment advice, financial advice, trading advice, or any other type of advice. DAIC does not recommend the purchase, sale, or holding of any cryptocurrency or other investment.


