In the evolving world of (PoS) blockchains, participants are always looking for ways to maximize the utility and potential rewards of their staked assets. Traditionally, staking involves locking up crypto to help secure a specific network. But what if those already-staked assets could perform additional security duties simultaneously? This is the core idea behind Restaking. For holders, the main appeal is the potential for layered rewards: earning base staking yield plus extra income from the third-party services they help secure. See our complete guide below for more information on the realm of Restaking.
Key Takeaways
- Double Duties: Restaking provides cryptocurrency funds already delegated to secure one network with the opportunity to secure other services or protocols at the same time.
- Shared Security Model: It allows new or custom protocols to "rent" or "borrow" security guarantees from established, older PoS systems, potentially reducing their barrier of entry.
- Multi-Layered Rewards: Players who opt to participate in these additional security workloads can gain additional rewards, stacked on top of their base staking return.
- Pioneering Uses: While the concept is versatile, protocols developed on established networks such as Ethereum have been pioneers in turning restaking models into practice (EigenLayer being an excellent example).
- Compounded Risk Exposure:Perhaps most crucial among the trade-offs is that restakers are exposed to compounds of risk; issues with the base network or any one of the supporting services rooted can initiate penalties (slashing).
So, What Exactly Is Restaking?

Fundamentally, Restaking is a method designed to extend the crypto-economic security of a PoS blockchain beyond its native purpose. In a typical Proof-of-Stake configuration, staked assets are collateral, validators risk losing this collateral (getting slashed) if they are malicious or reckless, thus incentivizing honest action. This economic security underpins the network's integrity.
Restaking proposes that this existing security guarantee – the value locked up and the associated slashing conditions – can be "re-purposed" or "re-hypothecated." Stakers can voluntarily agree to have their staked assets subject to additional slashing conditions tied to their performance in securing other protocols or services. These external systems are often referred to as Actively Validated Services (AVSs).
AVSs represent a wide range of potential applications: data availability layers, decentralized sequencers for rollups, oracle networks, bridges, novel execution environments, and more. These services require robust security, but might find it difficult or inefficient to establish their own independent validator sets and attract sufficient staked capital. By utilizing restaking, they can effectively inherit security from a larger pool of capital already committed to a base layer. In return for providing this security, restakers are typically compensated with fees or tokens from the AVSs.
The EigenLayer protocol, an Ethereum-based one, is the most widely used deployment that pioneered and popularized this model, creating a marketplace for this kind of shared security. But the underlying concept is not necessarily tied to one platform.
Fin out more about Eigenlayer in our Blog post: “Ultimate Guide to EigenLayer: Revolutionizing Ethereum Staking and Security”
How Does Restaking Work? The Nitty-Gritty
At their core, protocols enabling restaking or shared security provide frameworks for participants to opt-in and agree to specific terms, beyond base-layer consensus. While the technical details differ significantly across implementations, the ways participants engage generally fall into a few categories:
Direct Validator Participation (Native Stake): Under this approach, validators that are already securing an underlying PoS network can use their staked capital (their "native" stake) for additional security duties. By configuring their setup according to the respective protocol's specification, they take on the obligation of providing an extended security guarantee. Completion of these extra duties can receive extra rewards, but their failure can trigger penalties on their original stake on the underlying network. This method typically entails hands-on validator infrastructure management.
Using Liquid Staking Tokens (LSTs): To broaden participation beyond just validators, the majority of models allow for the use of Liquid Staking Tokens (LSTs). These are derivatives of staked assets, but are transferable and liquid. Their owners are able to deposit their LSTs in special smart contracts or platforms. The shared security protocol then leverages the economic value behind these deposited LSTs to secure external chains or services. This allows token holders to potentially gain extra rewards without operating validator nodes.
Managed Participation via Derivative Tokens (e.g., LRTs): Further streamlining the process, specialized platforms accept deposits of base assets or LSTs. The platforms then take care of the underlying intricacies of participation in one or more restaking or shared security systems – such as selecting services to secure and handling delegations. In return, the delegetor receives a new type of liquid derivative token (e.g., an LRT) representing their share of the managed pool and accruing composite rewards. While this adds simplicity and liquidity, it introduces reliance on the platform's specific strategy and security.
Leveraging External Collateral: Some shared security models address the problem in an entirely different way by leveraging collateral from entirely different ecosystems. For instance, solutions are being developed to use assets like Bitcoin, locked employing using cryptographic methods on their native chain, to provide economic security guarantees for Proof-of-Stake chains.
These different strategies outline how staked or outside capital can be leveraged to assist in defending multiple blockchains. Each of these methods provides a unique trade-off between ease of access, technical requirements, possible reward, and risk for users. These general mechanisms provide a foundation for examining specific protocols and ecosystems discussed later.
Here is an example of how restaking works within EigenLayer.
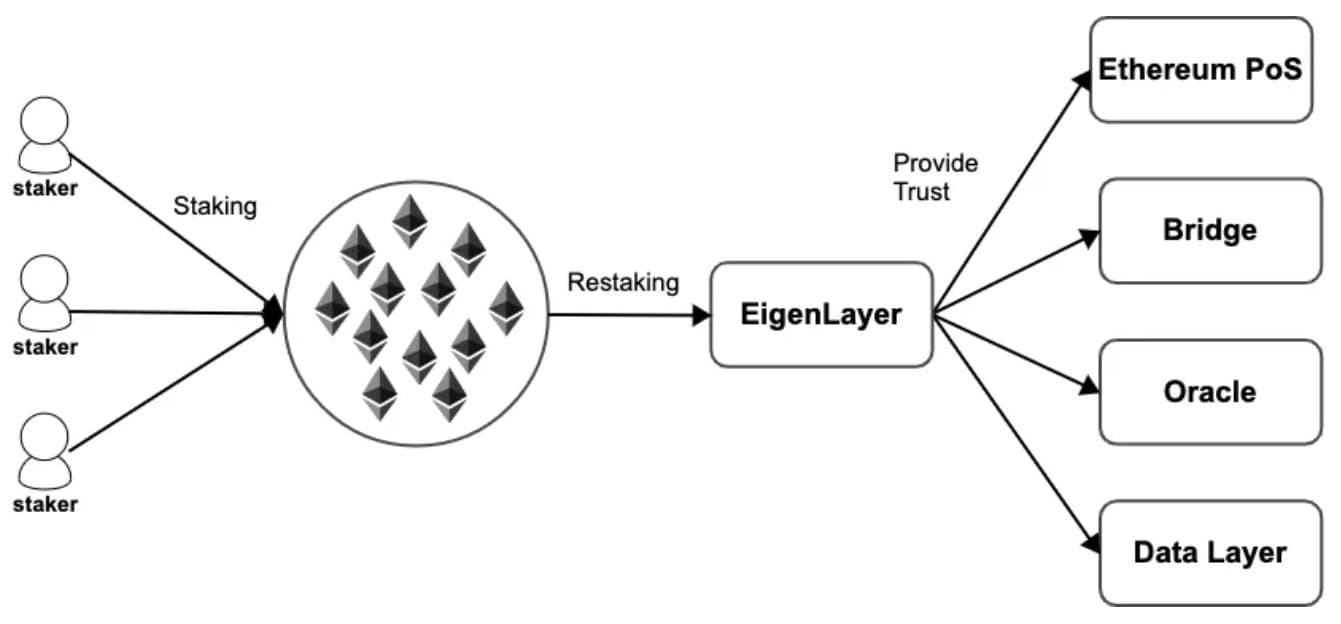
Key Advantages of the Restaking
Having clarified how restaking works, let's look at the key advantages this model makes available to participants and the broader ecosystem.
One major aspect is unlocking greater productivity from staked capital. Assets committed to network security, especially liquid staking tokens (LSTs), gain new functional roles. Apart from earning a base yield, they can be utilized to support other valuable services, with the potential to earn layered returns from various sources simultaneously from the same underlying base of capital. This shifts staked assets from fairly fixed components to more dynamic, multi-purpose assets in the digital economy.
Besides, restaking also aims to promote a more open and effective innovation environment. By allowing new protocols or core services (AVSs) to tap existing pools of economic security, it lowers considerably the barrier for constructing high-trust applications. Instead of facing the immense challenge of independently bootstrapping security, innovators can leverage existing trust networks. This shared security approach reduces fragmentation and, perhaps, overall lowers infrastructure securing costs, so developers can focus more on developing unique functionality.
In other words, the appeal lies in creating a more interconnected and efficient system in which capital is utilized more fully, and new services able to enjoy strong security more easily.
What Are the Risks of Restaking?
As with most things that have higher reward possibilities, restaking comes with some serious risks to take into consideration:
Compounded Slashing Risk: This remains the largest one. Users put themselves at risk of penalty by the base network, as well as from every AVS they secure. Failure with any such service may result in slashing of the main stake, so knowing the specific slashing rules is important.
Increased Complexity: The system contains a number of interacting levels of smart contracts and protocols. Bugs, exploits, or unanticipated adverse interactions at any level can cause economic loss. The overall complexity makes it difficult to thoroughly audit.
Centralization Risks: Restaking might result in accumulating capital to a small number of powerful validators or LRT protocols, potentially threatening bottlenecks or single points of failure, and undermining the network's decentralization.
Operator Risk: Members are relying on the ability and integrity of validators and/or LRT protocols to properly manage operations and risks. Choosing good operators is crucial.
Liquidity & Market Risks: LSTs and LRTs can be subject to de-pegging risks (price lower than the value of the underlying asset) and volatile market liquidity. Returns from restaking are not guaranteed and can vary.
Prospective users have to weigh these risks against potential benefits carefully.
The Restaking Ecosystem & Examples
So, where is restaking actually making waves? As of early 2025, platforms tracking the space, like DefiLlama, showcase significant capital – $14.5b in Total Value Locked (TVL) – flowing into restaking protocols and the layers built upon them.
This booming ecosystem is becoming increasingly diverse. We're seeing a fascinating landscape unfold, featuring core shared security platforms, a whole universe of Liquid Restaking Tokens (LRTs) offering simplified access, and innovative projects extending similar security concepts across different blockchain ecosystems or even leveraging assets like Bitcoin. Let's dive into the key players and examples defining this frontier.
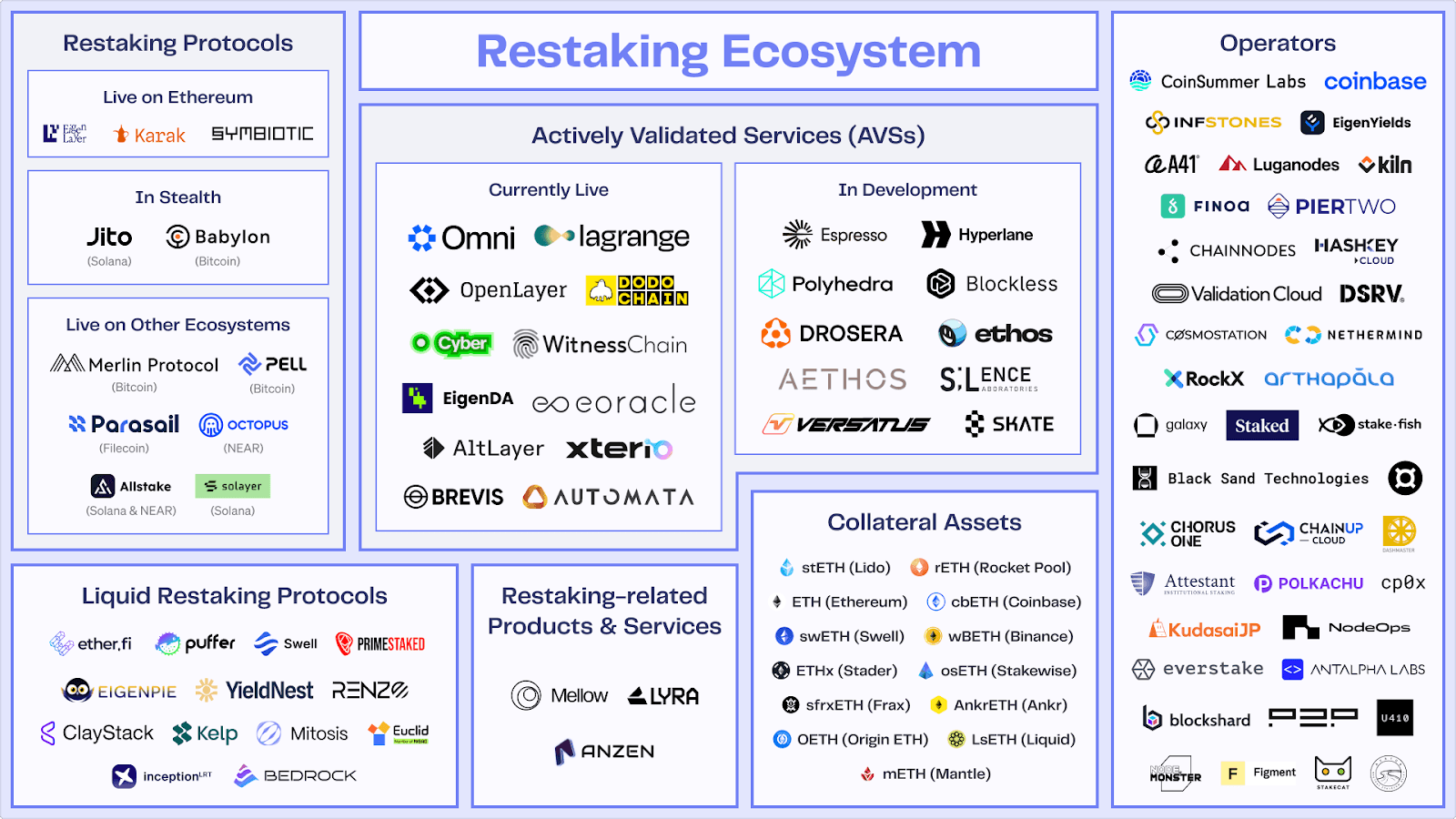
While the concept of shared security finds application broadly, the most developed restaking ecosystem currently revolves around Ethereum. This is largely driven by EigenLayer, which functions as the core marketplace connecting restakers with diverse AVSs like data availability layers (e.g., EigenDA), oracles, and bridges. Building upon EigenLayer, a vibrant group of LRT Protocols (such as Ether.fi, Renzo, Puffer, etc.) has also emerged, simplifying user access and managing billions in restaked assets within the Ethereum environment.
However, innovation in shared security extends significantly beyond this model. A major development involves leveraging Bitcoin's security for PoS chains, pioneered by Babylon Chain. This protocol allows Bitcoin's economic weight to secure other blockchains. This approach is especially relevant within the Cosmos ecosystem as its “Internet of Blockchains” vision fosters numerous application-specific chains that require robust yet accessible security, a challenge that shared security models like Babylon aim to address.
Furthermore, the landscape includes other emerging base protocols offering alternatives, such as the modular Symbiotic and the Layer 2 multi-asset Karak. The Solana ecosystem is another active area, featuring Jito Restaking (using Solana LSTs) and Solayer (securing Solana AVSs).
Final Thoughts: Innovation with Caveats
Restaking represents a significant conceptual advance in Proof-of-Stake systems, aiming to unlock greater capital efficiency and provide scalable security solutions. It offers an intriguing possibility for stakers to earn additional yield and for new protocols to deploy security more easily.
However, keep in mind that the ecosystem is actively experimenting, the "best practices" are still emerging, and the full implications are unfolding in real-time. Engaging with restaking today means participating in that experiment. It demands more than just surface-level understanding, it requires genuine diligence, a clear-eyed view of the heightened risks involved, and careful consideration of the security and strategies employed by any platform or service you interact with. It's a space brimming with innovation, but one where caution and thorough research are your most essential tools.
The information provided by DAIC, including but not limited to research, analysis, data, or other content, is offered solely for informational purposes and does not constitute investment advice, financial advice, trading advice, or any other type of advice. DAIC does not recommend the purchase, sale, or holding of any cryptocurrency or other investment.


